PRISM is a code name for a program under which the United States National Security Agency (NSA) collects internet communications from various U.S. internet companies.[1][2][3] The program is also known by the SIGAD US-984XN.[4][5] PRISM collects stored internet communications based on demands made to internet companies such as Google Inc. under Section 702 of the FISA Amendments Act of 2008 to turn over any data that match court-approved search terms.[6] The NSA can use these PRISM requests to target communications that were encrypted when they traveled across the internet backbone, to focus on stored data that telecommunication filtering systems discarded earlier,[7][8] and to get data that is easier to handle, among other things.[9]
PRISM began in 2007 in the wake of the passage of the Protect America Act under the Bush Administration.[10][11] The program is operated under the supervision of the U.S. Foreign Intelligence Surveillance Court (FISA Court, or FISC) pursuant to the Foreign Intelligence Surveillance Act (FISA).[12] Its existence was leakedsix years later by NSA contractor Edward Snowden, who warned that the extent of mass data collection was far greater than the public knew and included what he characterized as "dangerous" and "criminal" activities.[13] The disclosures were published by The Guardian and The Washington Post on June 6, 2013. Subsequent documents have demonstrated a financial arrangement between NSA's Special Source Operations division (SSO) and PRISM partners in the millions of dollars.[14]
Documents indicate that PRISM is "the number one source of raw intelligence used for NSA analytic reports", and it accounts for 91% of the NSA's internet traffic acquired under FISA section 702 authority."[15][16] The leaked information came to light one day after the revelation that the FISA Court had been ordering a subsidiary of telecommunications company Verizon Communications to turn over to the NSA logs tracking all of its customers' telephone calls.[17][18]
U.S. government officials have disputed some aspects of the Guardian and Washington Post stories and have defended the program by asserting it cannot be used on domestic targets without a warrant, that it has helped to prevent acts of terrorism, and that it receives independent oversight from the federal government's executive, judicial and legislative branches.[19][20] On June 19, 2013, U.S. President Barack Obama, during a visit to Germany, stated that the NSA's data gathering practices constitute "a circumscribed, narrow system directed at us being able to protect our people."[21]
Contents [hide]
1Media disclosure of PRISM
1.1The slides
2The program
2.1Extent of the program
2.2PRISM overview
3Responses to disclosures
3.1United States government
3.1.1Executive branch
3.1.2Legislative branch
3.1.3Judicial branch
3.1.4The U.S. military
3.2Responses and involvement of other countries
3.2.1Austria
3.2.2Australia
3.2.3Brazil
3.2.4Canada
3.2.5European Union
3.2.6France
3.2.7Germany
3.2.8Israel
3.2.9Mexico
3.2.10New Zealand
3.2.11Spain
3.2.12United Kingdom
3.3Companies
3.3.1Initial public statements
3.3.2Post-PRISM transparency reports
3.4Public and media response
3.4.1Domestic
3.4.2International
3.4.2.1China and Hong Kong
3.4.2.2Europe
3.4.2.3India
4Legal aspects
4.1Applicable law and practice
4.2Litigation
4.3Analysis of legal issues
4.4Legality of the FISA Amendments Act
5Programs sharing the name PRISM
6Related NSA programs
7See also
8Notes
9References
10External links
Media disclosure of PRISM[edit]
See also: Global surveillance disclosure
PRISM was publicly revealed when classified documents about the program were leaked to journalists of The Washington Post and The Guardian by Edward Snowden – at the time an NSA contractor – during a visit to Hong Kong.[1][2] The leaked documents included 41 PowerPoint slides, four of which were published in news articles.[1][2]
The documents identified several technology companies as participants in the PRISM program, including Microsoft in 2007, Yahoo! in 2008, Google in 2009, Facebook in 2009, Paltalk in 2009, YouTube in 2010, AOL in 2011, Skype in 2011 and Apple in 2012.[22] The speaker's notes in the briefing document reviewed by The Washington Post indicated that "98 percent of PRISM production is based on Yahoo, Google, and Microsoft".[1]
The slide presentation stated that much of the world's electronic communications pass through the U.S., because electronic communications data tend to follow the least expensive route rather than the most physically direct route, and the bulk of the world's internet infrastructure is based in the United States.[15] The presentation noted that these facts provide United States intelligence analysts with opportunities for intercepting the communications of foreign targets as their electronic data pass into or through the United States.[2][15]
Snowden's subsequent disclosures included statements that government agencies such as the United Kingdom's GCHQ also undertook mass interception and tracking of internet and communications data[23] – described by Germany as "nightmarish" if true[24] – allegations that the NSA engaged in "dangerous" and "criminal" activity by "hacking" civilian infrastructure networks in other countries such as "universities, hospitals, and private businesses",[13] and alleged that compliance offered only very limited restrictive effect on mass data collection practices (including of Americans) since restrictions "are policy-based, not technically based, and can change at any time", adding that "Additionally, audits are cursory, incomplete, and easily fooled by fake justifications",[13] with numerous self-granted exceptions, and that NSA policies encourage staff to assume the benefit of the doubt in cases of uncertainty.[25][26][27]
The slides[edit]
Below are a number of slides released by Edward Snowden showing the operation and processes behind the PRISM program. It should be noted that the "FAA" referred to is Section 702 of the FISA Amendments Act ("FAA"), and not the Federal Aviation Administration, which is more widely known by the same FAA initialism.

Introduction slide.

Slide showing that much of the world's communications flow through the U.S.

Details of information collected via PRISM

Slide listing companies and the date that PRISM collection began
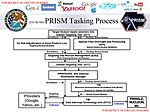
Slide showing PRISM's tasking process

Slide showing the PRISM collection dataflow

Slide showing PRISM case numbers

Slide showing the REPRISMFISA Web app

Slide showing some PRISM targets.

Slide fragment mentioning "upstream collection", FAA702, EO 12333, and references yahoo.com explicitly in the text.

FAA702 Operations, and map

FAA702 Operations, and map. The subheader reads "Collection only possible under FAA702 Authority". FAIRVIEW is in the center box.

FAA702 Operations, and map. The subheader reads "Collection only possible under FAA702 Authority". STORMBREW is in the center box.

Tasking, Points to Remember. Transcript of body: Whenever your targets meet FAA criteria, you should consider asking to FAA. Emergency tasking processes exist for [imminent /immediate ] threat to life situations and targets can be placed on [illegible] within hours (surveillance and stored comms). Get to know your Product line FAA adjudicators and FAA leads.
The French newspaper Le Monde disclosed new PRISM slides (See Page 4, 7 and 8) coming from the "PRISM/US-984XN Overview" presentation on October 21, 2013.[28] The British newspaper The Guardiandisclosed new PRISM slides (see pages 3 and 6) in November 2013 which on the one hand compares PRISM with the Upstream program, and on the other hand deals with collaboration between the NSA's Threat Operations Center and the FBI.[29]
Wikimedia Commons keeps copies of the leaked PowerPoint slides here : Commons:Category:PRISM (surveillance program) along with other associated documents.
The program[edit]

PRISM logo
PRISM is a program from the Special Source Operations (SSO) division of the NSA, which in the tradition of NSA's intelligence alliances, cooperates with as many as 100 trusted U.S. companies since the 1970s.[1] A prior program, the Terrorist Surveillance Program,[30][31] was implemented in the wake of the September 11 attacksunder the George W. Bush Administration but was widely criticized and challenged as illegal, because it did not include warrants obtained from the Foreign Intelligence Surveillance Court.[31][32][33][34][35] PRISM was authorized by the Foreign Intelligence Surveillance Court.[15]
PRISM was enabled under President Bush by the Protect America Act of 2007 and by the FISA Amendments Act of 2008, which immunizes private companies from legal action when they cooperate with U.S. government agencies in intelligence collection. In 2012 the act was renewed by Congress under President Obama for an additional five years, through December 2017.[2][36][37] According to The Register, the FISA Amendments Act of 2008 "specifically authorizes intelligence agencies to monitor the phone, email, and other communications of U.S. citizens for up to a week without obtaining a warrant" when one of the parties is outside the U.S.[36]
The most detailed description of the PRISM program can be found in a report about NSA's collection efforts under Section 702 FAA, that was released by the Privacy and Civil Liberties Oversight Board (PCLOB) on July 2, 2014.[38]
According to this report, PRISM is only used to collect internet communications, not telephone conversations. These internet communications are not collected in bulk, but in a targeted way: only communications that are to or from specific selectors, like e-mail addresses, can be gathered. Under PRISM, there's no collection based upon keywords or names.[38]
The actual collection process is done by the Data Intercept Technology Unit (DITU) of the FBI, which on behalf of the NSA sends the selectors to the US Internet service providers, which were previously served with a Section 702 Directive. Under this directive, the provider is legally obliged to hand over (to DITU) all communications to or from the selectors provided by the government.[38] DITU then sends these communications to NSA, where they are stored in various databases, depending on their type.
Data, both content and metadata, that already have been collected under the PRISM program, may be searched for both US and non-US person identifiers. These kinds of queries became known as "back-door searches" and are conducted by NSA, FBI and CIA.[39] Each of these agencies has slightly different protocols and safeguards to protect searches with a US person identifier.[38]
Extent of the program[edit]
Internal NSA presentation slides included in the various media disclosures show that the NSA could unilaterally access data and perform "extensive, in-depth surveillance on live communications and stored information" with examples including email, video and voice chat, videos, photos, voice-over-IP chats (such as Skype), file transfers, and social networking details.[2] Snowden summarized that "in general, the reality is this: if an NSA, FBI, CIA, DIA, etc. analyst has access to query raw SIGINT [signals intelligence] databases, they can enter and get results for anything they want."[13]
According to The Washington Post, the intelligence analysts search PRISM data using terms intended to identify suspicious communications of targets whom the analysts suspect with at least 51 percent confidence to not be U.S. citizens, but in the process, communication data of some U.S. citizens are also collected unintentionally.[1] Training materials for analysts tell them that while they should periodically report such accidental collection of non-foreign U.S. data, "it's nothing to worry about."[1][40]
According to The Guardian, NSA had access to chats and emails on Hotmail.com, Skype, because Microsoft had "developed a surveillance capability to deal" with the interception of chats, and "for Prism collection against Microsoft email services will be unaffected because Prism collects this data prior to encryption."[41][42][43]
Also according to The Guardian's Glenn Greenwald even low-level NSA analysts are allowed to search and listen to the communications of Americans and other people without court approval and supervision. Greenwald said low level Analysts can, via systems like PRISM, "listen to whatever emails they want, whatever telephone calls, browsing histories, Microsoft Word documents.[30] And it's all done with no need to go to a court, with no need to even get supervisor approval on the part of the analyst."[44]
He added that the NSA databank, with its years of collected communications, allows analysts to search that database and listen "to the calls or read the emails of everything that the NSA has stored, or look at the browsing histories or Google search terms that you've entered, and it also alerts them to any further activity that people connected to that email address or that IP address do in the future."[44] Greenwald was referring in the context of the foregoing quotes to the NSA program X-Keyscore.[45]
PRISM overview[edit]
DesignationLegal AuthoritySee NoteKey TargetsType of Information collectedAssociated DatabasesAssociated SoftwareUS-984XN Section 702 of the FISA Amendments Act (FAA) Known Targets include[46]
Venezuela
Military procurement
Oil
Mexico
Narcotics
Energy
Internal Security
Political Affairs
Colombia
Trafficking
FARC The exact type of data varies by provider:
Chat – video, voice
Videos
Stored data
VoIP
File transfers
Video Conferencing
Notifications of target activity, logins, etc.
Online Social Networking details
Special Requests Known:
TRAFFICTHIEF
MARINA
MAINWAY
FALLOUT
PINWALE
CONVEYANCE
NUCLEON Known:
Unified Targeting Tool
Responses to disclosures[edit]
United States government[edit]
Executive branch[edit]
Shortly after publication of the reports by The Guardian and The Washington Post, the United States Director of National Intelligence, James Clapper, on June 7, 2013 released a statement confirming that for nearly six years the government of the United States had been using large Internet services companies such as Facebook to collect information on foreigners outside the United States as a defense against national security threats.[17] The statement read in part, "The Guardian and The Washington Post articles refer to collection of communications pursuant to Section 702 of the Foreign Intelligence Surveillance Act. They contain numerous inaccuracies."[47] He went on to say, "Section 702 is a provision of FISA that is designed to facilitate the acquisition of foreign intelligence information concerning non-U.S. persons located outside the United States. It cannot be used to intentionally target any U.S. citizen, any other U.S. person, or anyone located within the United States."[47] Clapper concluded his statement by stating, "The unauthorized disclosure of information about this important and entirely legal program is reprehensible and risks important protections for the security of Americans."[47] On March 12, 2013, Clapper had told the United States Senate Select Committee on Intelligence that the NSA does "not wittingly" collect any type of data on millions or hundreds of millions of Americans.[48] Clapper later admitted the statement he made on March 12, 2013 was a lie,[49] or in his words "I responded in what I thought was the most truthful, or least untruthful manner by saying no."[50]
On June 7, 2013 U.S. President Barack Obama, referring to the PRISM program[citation needed] and the NSA's telephone calls logging program, said, "What you've got is two programs that were originally authorized by Congress, have been repeatedly authorized by Congress. Bipartisan majorities have approved them. Congress is continually briefed on how these are conducted. There are a whole range of safeguards involved. And federal judges are overseeing the entire program throughout."[51] He also said, "You can't have 100 percent security and then also have 100 percent privacy and zero inconvenience. You know, we're going to have to make some choices as a society."[51] In separate statements, senior Obama administration officials (not mentioned by name in source) said that Congress had been briefed 13 times on the programs since 2009.[52]
On June 8, 2013, Director of National Intelligence Clapper made an additional public statement about PRISM and released a fact sheet providing further information about the program, which he described as "an internal government computer system used to facilitate the government's statutorily authorized collection of foreign intelligence information from electronic communication service providers under court supervision, as authorized by Section 702 of the Foreign Intelligence Surveillance Act (FISA) (50 U.S.C. § 1881a)."[53][54] The fact sheet stated that "the surveillance activities published in The Guardian and the Washington Post are lawful and conducted under authorities widely known and discussed, and fully debated and authorized by Congress."[53] The fact sheet also stated that "the United States Government does not unilaterally obtain information from the servers of U.S. electronic communication service providers. All such information is obtained with FISA Court approval and with the knowledge of the provider based upon a written directive from the Attorney General and the Director of National Intelligence." It said that the Attorney General provides FISA Court rulings and semi-annual reports about PRISM activities to Congress, "provid[ing] an unprecedented degree of accountability and transparency."[53] Democratic Senators Udall and Wyden, who serve on the U.S. Senate Select Committee on Intelligence, subsequently criticized the fact sheet as being inaccurate.[clarification needed] NSA Director General Keith Alexander acknowledged the errors, stating that the fact sheet "could have more precisely described" the requirements governing the collection of e-mail and other internet content from U.S. companies. The fact sheet was withdrawn from the NSA's website around June 26.[55]
In a closed-doors Senate hearing around June 11, FBI Director Robert Mueller said that Snowden's leaks had caused "significant harm to our nation and to our safety."[56] In the same Senate NSA Director Alexander defended the program.[further explanation needed] Alexander's defense was immediately criticized by Senators Udall and Wyden, who said they saw no evidence that the NSA programs had produced "uniquely valuable intelligence." In a joint statement, they wrote, "Gen Alexander's testimony yesterday suggested that the NSA's bulk phone records collection program helped thwart 'dozens' of terrorist attacks, but all of the plots that he mentioned appear to have been identified using other collection methods."[56][57]
On June 18, NSA Director Alexander said in an open hearing before the House Intelligence Committee of Congress that communications surveillance had helped prevent more than 50 potential terrorist attacks worldwide (at least 10 of them involving terrorism suspects or targets in the United States) between 2001 and 2013, and that the PRISM web traffic surveillance program contributed in over 90 percent of those cases.[58][59][60] According to court records, one example Alexander gave regarding a thwarted attack by al Qaeda on the New York Stock Exchange was not in fact foiled by surveillance.[61] Several senators wrote Director of National Intelligence Clapper asking him to provide other examples.[62]
U.S. intelligence officials, speaking on condition of anonymity, told various news outlets that by June 24 they were already seeing what they said was evidence that suspected terrorists had begun changing their communication practices in order to evade detection by the surveillance tools disclosed by Snowden.[63][64]
Legislative branch[edit]
In contrast to their swift and forceful reactions the previous day to allegations that the government had been conducting surveillance of United States citizens' telephone records, Congressional leaders initially had little to say about the PRISM program the day after leaked information about the program was published. Several lawmakers declined to discuss PRISM, citing its top-secret classification,[65] and others said that they had not been aware of the program.[66] After statements had been released by the President and the Director of National Intelligence, some lawmakers began to comment:
Senator John McCain (R-AZ)
June 9, 2013 "We passed the Patriot Act. We passed specific provisions of the act that allowed for this program to take place, to be enacted in operation."[67]
Senator Dianne Feinstein (D-CA), chair of the Senate Intelligence Committee
June 9 "These programs are within the law," "part of our obligation is keeping Americans safe," "Human intelligence isn't going to do it."[68]
June 9 "Here's the rub: the instances where this has produced good—has disrupted plots, prevented terrorist attacks, is all classified, that's what's so hard about this."[69]
June 11 "It went fine. ... We asked him (Keith Alexander) to declassify things because it would be helpful (for people and lawmakers to better understand the intelligence programs). ... I've just got to see if the information gets declassified. I'm sure people will find it very interesting."[70]
Senator Rand Paul (R-KY)
June 9 "I'm going to be seeing if I can challenge this at the Supreme Court level. I'm going to be asking the internet providers and all of the phone companies: ask your customers to join me in a class-action lawsuit."[67]
Senator Susan Collins (R-ME), member of Senate Intelligence Committee and past member of Homeland Security Committee
June 11 "I had, along with Joe Lieberman, a monthly threat briefing, but I did not have access to this highly compartmentalized information" and "How can you ask when you don't know the program exists?"[71]
Representative Jim Sensenbrenner (R-WI), principal sponsor of the Patriot Act
June 9, "This is well beyond what the Patriot Act allows."[72] "President Obama's claim that 'this is the most transparent administration in history' has once again proven false. In fact, it appears that no administration has ever peered more closely or intimately into the lives of innocent Americans."[72]
Representative Mike Rogers (R-MI), a Chairman of the Permanent Select Committee on Intelligence.
June 9 "One of the things that we're charged with is keeping America safe and keeping our civil liberties and privacy intact. I think we have done both in this particular case."[68]
June 9 "Within the last few years this program was used to stop a program, excuse me, to stop a terrorist attack in the United States, we know that. It's, it's, it's important, it fills in a little seam that we have and it's used to make sure that there is not an international nexus to any terrorism event that they may believe is ongoing in the United States. So in that regard it is a very valuable thing."[73]
Senator Mark Udall (D-CO)
June 9 "I don't think the American public knows the extent or knew the extent to which they were being surveilled and their data was being collected. ... I think we ought to reopen the Patriot Act and put some limits on the amount of data that the National Security (Agency) is collecting. ... It ought to remain sacred, and there's got to be a balance here. That is what I'm aiming for. Let's have the debate, let's be transparent, let's open this up."[68]
Representative Todd Rokita (R-IN)
June 10 "We have no idea when they [Foreign Intelligence Surveillance Court] meet, we have no idea what their judgments are."[74]
Representative Luis Gutierrez (D-IL)
June 9 "We will be receiving secret briefings and we will be asking, I know I'm going to be asking to get more information. I want to make sure that what they're doing is harvesting information that is necessary to keep us safe and not simply going into everybody's private telephone conversations and Facebook and communications. I mean one of the, you know, the terrorists win when you debilitate freedom of expression and privacy."[73]
Senator Ron Wyden (D-OR)
July 11 "I have a feeling that the administration is getting concerned about the bulk phone records collection, and that they are thinking about whether to move administratively to stop it. I think we are making a comeback".[75]
Following these statements some lawmakers from both parties warned national security officials during a hearing before the House Judiciary Committee that they must change their use of sweeping National Security Agency surveillance programs or face losing the provisions of the Foreign Intelligence Surveillance Act that have allowed for the agency's mass collection of telephone metadata.[76] "Section 215 expires at the end of 2015, and unless you realize you've got a problem, that is not going to be renewed," Rep. Jim Sensenbrenner, R-Wis., author of the USA Patriot Act, threatened during the hearing.[76] "It's got to be changed, and you've got to change how you operate section 215. Otherwise, in two and a half years, you're not going to have it anymore."[76]
Judicial branch[edit]
Leaks of classified documents pointed to the role of a special court in enabling the government's secret surveillance programs, but members of the court maintained they were not collaborating with the executive branch.[77] The New York Times, however, reported in July 2013 that in "more than a dozen classified rulings, the nation's surveillance court has created a secret body of law giving the National Security Agency the power to amass vast collections of data on Americans while pursuing not only terrorism suspects, but also people possibly involved in nuclear proliferation, espionage and cyberattacks."[78]After Members of the U.S. Congress pressed the Foreign Intelligence Surveillance Court to release declassified versions of its secret ruling, the court dismissed those requests arguing that the decisions can't be declassified because they contain classified information.[79] Reggie Walton, the current FISA presiding judge, said in a statement: "The perception that the court is a rubber stamp is absolutely false. There is a rigorous review process of applications submitted by the executive branch, spearheaded initially by five judicial branch lawyers who are national security experts, and then by the judges, to ensure that the court's authorizations comport with what the applicable statutes authorize."[80] The accusation of being a "rubber stamp" was further rejected by Walton who wrote in a letter to Senator Patrick J. Leahy: "The annual statistics provided to Congress by the Attorney General [...]—frequently cited to in press reports as a suggestion that the Court's approval rate of application is over 99%—reflect only the number of finalapplications submitted to and acted on by the Court. These statistics do not reflect the fact that many applications are altered to prior or final submission or even withheld from final submission entirely, often after an indication that a judge would not approve them."[81]
The U.S. military[edit]
The U.S. military has acknowledged blocking access to parts of The Guardian website for thousands of defense personnel across the country,[82] and blocking the entire Guardian website for personnel stationed throughout Afghanistan, the Middle East, and South Asia.[83] A spokesman said the military was filtering out reports and content relating to government surveillance programs to preserve "network hygiene" and prevent any classified material from appearing on unclassified parts of its computer systems.[82] Access to the Washington Post, which also published information on classified NSA surveillance programs disclosed by Edward Snowden, had not been blocked at the time the blocking of access to The Guardian was reported.[83]
Responses and involvement of other countries[edit]
Austria[edit]
The former head of the Austrian Federal Office for the Protection of the Constitution and Counterterrorism, Gert-René Polli, stated he knew the PRISM program under a different name and stated that surveillance activities had occurred in Austria as well. Polli had publicly stated in 2009 that he had received requests from US intelligence agencies to do things that would be in violation of Austrian law, which Polli refused to allow.[84][85]
Australia[edit]
The Australian government has said it will investigate the impact of the PRISM program and the use of the Pine Gap surveillance facility on the privacy of Australian citizens.[86] Australia's former foreign minister Bob Carr said that Australians shouldn't be concerned about PRISM but that cybersecurity is high on the government's list of concerns.[87] The Australian Foreign Minister Julie Bishop stated that the acts of Edward Snowden were treachery and offered a staunch defence of her nation's intelligence co-operation with the United States.[88]
Brazil[edit]
Brazil's president at the time, Dilma Rousseff, responded to Snowden's reports that the NSA spied on her phone calls and emails by cancelling a planned October 2013 state visit to the United States, demanding an official apology, which by October 20, 2013, hadn't come.[89] Also, Rousseff classified the spying as unacceptable between more harsh words in a speech before the UN General Assembly on September 24, 2013.[90] As a result, Boeing lost out on a US$4.5 billion contract for fighter jets to Sweden's Saab Group.[91]
Canada[edit]

CSE headquarters in Ottawa
Canada's national cryptologic agency, the Communications Security Establishment (CSE), said that commenting on PRISM "would undermine CSE's ability to carry out its mandate." Privacy Commissioner Jennifer Stoddart lamented Canada's standards when it comes to protecting personal online privacy stating "We have fallen too far behind" in her report. "While other nations' data protection authorities have the legal power to make binding orders, levy hefty fines and take meaningful action in the event of serious data breaches, we are restricted to a 'soft' approach: persuasion, encouragement and, at the most, the potential to publish the names of transgressors in the public interest." And, "when push comes to shove," Stoddart wrote, "short of a costly and time-consuming court battle, we have no power to enforce our recommendations."[92][93]
European Union[edit]
On 20 October 2013 a committee at the European Parliament backed a measure that, if it is enacted, would require American companies to seek clearance from European officials before complying with United States warrants seeking private data. The legislation has been under consideration for two years. The vote is part of efforts in Europe to shield citizens from online surveillance in the wake of revelations about a far-reaching spying program by the U.S. National Security Agency.[94] Germany and France have also had ongoing mutual talks about how they can keep European email traffic from going across American servers.[95]
France[edit]
On October 21, 2013 the French Foreign Minister, Laurent Fabius, summoned the U.S. Ambassador, Charles Rivkin, to the Quai d'Orsay in Paris to protest large-scale spying on French citizens by the U.S. National Security Agency (NSA). Paris prosecutors had opened preliminary inquiries into the NSA program in July, but Fabius said, "… obviously we need to go further" and "we must quickly assure that these practices aren't repeated."[96]
Germany[edit]
Germany did not receive any raw PRISM data, according to a Reuters report.[97] German Chancellor Angela Merkel said that "the internet is new to all of us" to explain the nature of the program; Matthew Schofield of McClatchy Washington Bureau said, "She was roundly mocked for that statement."[98] Gert-René Polli, a former Austrian counter-terrorism official, said in 2013 that it is "absurd and unnatural" for the German authorities to pretend not to have known anything.[84][85] The German Army was using PRISM to support its operations in Afghanistan as early as 2011.[99]
In October 2013, it was reported that the NSA monitored Merkel's cell phone.[100] The United States denied the report, but following the allegations, Merkel called President Obama and told him that spying on friends was "never acceptable, no matter in what situation."[101]
Israel[edit]
Israeli newspaper Calcalist discussed[102] the Business Insider article[103] about the possible involvement of technologies from two secretive Israeli companies in the PRISM program—Verint Systems and Narus.
Mexico[edit]
After finding out about the PRISM program, the Mexican Government has started constructing its own spying program to spy on its own citizens. According to Jenaro Villamil, a writer from Procesco, CISEN, Mexico's intelligence agency has started to work with IBM and Hewlett Packard to develop its own data gathering software. "Facebook, Twitter, Emails and other social network sites are going to be priority."[104]
New Zealand[edit]
In New Zealand, University of Otago information science Associate Professor Hank Wolfe said that "under what was unofficially known as the Five Eyes Alliance, New Zealand and other governments, including the United States, Australia, Canada, and Britain, dealt with internal spying by saying they didn't do it. But they have all the partners doing it for them and then they share all the information."[105]
Edward Snowden, in a live streamed Google Hangout to Kim Dotcom and Julian Assange, alleged that he had received intelligence from New Zealand, and the NSA has listening posts in New Zealand.[106]
Spain[edit]
At a meeting of European Union leaders held the week of 21 October 2013, Mariano Rajoy, Spain's prime minister, said that "spying activities aren't proper among partner countries and allies". On 28 October 2013 the Spanish government summoned the American ambassador, James Costos, to address allegations that the U.S. had collected data on 60 million telephone calls in Spain. Separately, Íñigo Méndez de Vigo, a Spanish secretary of state, referred to the need to maintain "a necessary balance" between security and privacy concerns, but said that the recent allegations of spying, "if proven to be true, are improper and unacceptable between partners and friendly countries".[107]
United Kingdom[edit]
Further information: Mass surveillance in the United Kingdom
In the United Kingdom, the Government Communications Headquarters (GCHQ), which also has its own surveillance program, Tempora, had access to the PRISM program on or before June 2010 and wrote 197 reports with it in 2012 alone. The Intelligence and Security Committee of the UK Parliament reviewed the reports GCHQ produced on the basis of intelligence sought from the US. They found in each case a warrant for interception was in place in accordance with the legal safeguards contained in UK law.[108]
In August 2013, The Guardian newspaper's offices were visited by agents from GCHQ, who ordered and supervised the destruction of the hard drives containing information acquired from Snowden.[109]
Companies[edit]
The original Washington Post and Guardian articles reporting on PRISM noted that one of the leaked briefing documents said PRISM involves collection of data "directly from the servers" of several major Internet services providers.[1][2]
Initial public statements[edit]
Corporate executives of several companies identified in the leaked documents told The Guardian that they had no knowledge of the PRISM program in particular and also denied making information available to the government on the scale alleged by news reports.[2][110] Statements of several of the companies named in the leaked documents were reported by TechCrunch and The Washington Post as follows:[111][112]
Microsoft: "We provide customer data only when we receive a legally binding order or subpoena to do so, and never on a voluntary basis. In addition we only ever comply with orders for requests about specific accounts or identifiers. If the government has a broader voluntary national security program to gather customer data we don't participate in it."[111][113]
Yahoo!: "Yahoo! takes users' privacy very seriously. We do not provide the government with direct access to our servers, systems, or network."[111] "Of the hundreds of millions of users we serve, an infinitesimal percentage will ever be the subject of a government data collection directive."[112]
Facebook: "We do not provide any government organization with direct access to Facebook servers. When Facebook is asked for data or information about specific individuals, we carefully scrutinize any such request for compliance with all applicable laws, and provide information only to the extent required by law."[111]
Google: "Google cares deeply about the security of our users' data. We disclose user data to government in accordance with the law, and we review all such requests carefully. From time to time, people allege that we have created a government 'back door' into our systems, but Google does not have a backdoor for the government to access private user data."[111] "[A]ny suggestion that Google is disclosing information about our users' internet activity on such a scale is completely false."[112]
Apple: "We have never heard of PRISM. We do not provide any government agency with direct access to our servers, and any government agency requesting customer data must get a court order."[114]
Dropbox: "We've seen reports that Dropbox might be asked to participate in a government program called PRISM. We are not part of any such program and remain committed to protecting our users' privacy."[111]
In response to the technology companies' denials of the NSA being able to directly access the companies' servers, The New York Times reported that sources had stated the NSA was gathering the surveillance data from the companies using other technical means in response to court orders for specific sets of data.[17] The Washington Post suggested, "It is possible that the conflict between the PRISM slides and the company spokesmen is the result of imprecision on the part of the NSA author. In another classified report obtained by The Post, the arrangement is described as allowing 'collection managers [to send] content tasking instructions directly to equipment installed at company-controlled locations,' rather than directly to company servers."[1] "[I]n context, 'direct' is more likely to mean that the NSA is receiving data sent to them deliberately by the tech companies, as opposed to intercepting communications as they're transmitted to some other destination.[112]
"If these companies received an order under the FISA amendments act, they are forbidden by law from disclosing having received the order and disclosing any information about the order at all," Mark Rumold, staff attorney at the Electronic Frontier Foundation, told ABC News.[115]
On May 28, 2013, Google was ordered by United States District Court Judge Susan Illston to comply with a National Security Letter issued by the FBI to provide user data without a warrant.[116] Kurt Opsahl, a senior staff attorney at the Electronic Frontier Foundation, in an interview with VentureBeat said, "I certainly appreciate that Google put out a transparency report, but it appears that the transparency didn't include this. I wouldn't be surprised if they were subject to a gag order."[117]
The New York Times reported on June 7, 2013, that "Twitter declined to make it easier for the government. But other companies were more compliant, according to people briefed on the negotiations."[118] The other companies held discussions with national security personnel on how to make data available more efficiently and securely.[118] In some cases, these companies made modifications to their systems in support of the intelligence collection effort.[118] The dialogues have continued in recent months, as General Martin Dempsey, the chairman of the Joint Chiefs of Staff, has met with executives including those at Facebook, Microsoft, Google and Intel.[118] These details on the discussions provide insight into the disparity between initial descriptions of the government program including a training slide which states, "Collection directly from the servers"[119] and the companies' denials.[118]
While providing data in response to a legitimate FISA request approved by the FISA Court is a legal requirement, modifying systems to make it easier for the government to collect the data is not. This is why Twitter could legally decline to provide an enhanced mechanism for data transmission.[118] Other than Twitter, the companies were effectively asked to construct a locked mailbox and provide the key to the government, people briefed on the negotiations said.[118] Facebook, for instance, built such a system for requesting and sharing the information.[118] Google does not provide a lockbox system, but instead transmits required data by hand delivery or ssh.[120]
Post-PRISM transparency reports[edit]
In response to the publicity surrounding media reports of data-sharing, several companies requested permission to reveal more public information about the nature and scope of information provided in response to National Security requests.
On June 14, 2013, Facebook reported that the U.S. government had authorized the communication of "about these numbers in aggregate, and as a range." In a press release posted to its web site, the company reported, "For the six months ending December 31, 2012, the total number of user-data requests Facebook received from any and all government entities in the U.S. (including local, state, and federal, and including criminal and national security-related requests) – was between 9,000 and 10,000." The company further reported that the requests impacted "between 18,000 and 19,000" user accounts, a "tiny fraction of one percent" of more than 1.1 billion active user accounts.[121]
That same day, Microsoft reported that for the same period, it received "between 6,000 and 7,000 criminal and national security warrants, subpoenas and orders affecting between 31,000 and 32,000 consumer accounts from U.S. governmental entities (including local, state and federal)" which impacted "a tiny fraction of Microsoft's global customer base."[122]
Google issued a statement criticizing the requirement that data be reported in aggregated form, stating that lumping national security requests with criminal request data would be "a step backwards" from its previous, more detailed practices on its website's transparency report. The company said that it would continue to seek government permission to publish the number and extent of FISA requests.[123]
Cisco Systems saw a huge drop in export sales because of fears that the National Security Agency could be using backdoors in its products.[124]
On September 12, 2014, Yahoo! reported the U.S. Government threatened the imposition of $250,000 in fines per day if Yahoo didn't hand over user data as part of the NSA's PRISM program.[125] It is not known if other companies were threatened or fined for not providing data in response to a legitimate FISA requests.
Public and media response[edit]
Domestic[edit]

An elaborate graffito in Columbus, Ohio, United States, satirizing comprehensive surveillance of telecommunications.
The New York Times editorial board charged that the Obama administration "has now lost all credibility on this issue,"[126] and lamented that "for years, members of Congress ignored evidence that domestic intelligence-gathering had grown beyond their control, and, even now, few seem disturbed to learn that every detail about the public's calling and texting habits now reside in a N.S.A. database."[127] It wrote with respect to the FISA-Court in context of PRISM that it is "a perversion of the American justice system" when "judicial secrecy is coupled with a one-sided presentation of the issues."[128] According to the New York Times, "the result is a court whose reach is expanding far beyond its original mandate and without any substantive check."[128]
James Robertson, a former federal district judge based in Washington who served on the secret Foreign Intelligence Surveillance Act court for three years between 2002 and 2005 and who ruled against the Bush administration in the landmark Hamdan v. Rumsfeld case, said FISA court is independent but flawed because only the government's side is represented effectively in its deliberations. "Anyone who has been a judge will tell you a judge needs to hear both sides of a case," said James Robertson.[129] Without this judges do not benefit from adversarial debate. He suggested creating an advocate with security clearance who would argue against government filings.[130] Robertson questioned whether the secret FISA court should provide overall legal approval for the surveillance programs, saying the court "has turned into something like an administrative agency." Under the changes brought by the Foreign Intelligence Surveillance Act of 1978 Amendments Act of 2008, which expanded the US government's authority by forcing the court to approve entire surveillance systems and not just surveillance warrants as it previously handled, "the court is now approving programmatic surveillance. I don't think that is a judicial function."[129] Robertson also said he was "frankly stunned" by the New York Times report[78] that FISA court rulings had created a new body of law broadening the ability of the NSA to use its surveillance programs to target not only terrorists but suspects in cases involving espionage, cyberattacks and weapons of mass destruction.[129]
Former CIA analyst Valerie Plame Wilson and former U.S. diplomat Joseph Wilson, writing in an op-ed article published in The Guardian, said that "Prism and other NSA data-mining programs might indeed be very effective in hunting and capturing actual terrorists, but we don't have enough information as a society to make that decision."[131]
The Electronic Frontier Foundation (EFF), an international non-profit digital-rights group based in the U.S., is hosting a tool, by which an American resident can write to their government representatives regarding their opposition to mass spying.[132]
The Obama administration's argument that NSA surveillance programs such as PRISM and Boundless Informant had been necessary to prevent acts of terrorism was challenged by several parties. Ed Pilkington and Nicholas Watt of The Guardian said of the case of Najibullah Zazi, who had planned to bomb the New York City Subway, that interviews with involved parties and U.S. and British court documents indicated that the investigation into the case had actually been initiated in response to "conventional" surveillance methods such as "old-fashioned tip-offs" of the British intelligence services, rather than to leads produced by NSA surveillance.[133] Michael Daly of The Daily Beast stated that even though Tamerlan Tsarnaev, who conducted the Boston Marathon bombing with his brother Dzhokhar Tsarnaev, had visited the Al Qaeda-affiliated Inspire magazine website, and even though Russian intelligence officials had raised concerns with U.S. intelligence officials about Tamerlan Tsarnaev, PRISM did not prevent him from carrying out the Boston attacks. Daly observed that, "The problem is not just what the National Security Agency is gathering at the risk of our privacy but what it is apparently unable to monitor at the risk of our safety."[134]
Ron Paul, a former Republican member of Congress and prominent libertarian, thanked Snowden and Greenwald and denounced the mass surveillance as unhelpful and damaging, urging instead more transparency in U.S. government actions.[135] He called Congress "derelict in giving that much power to the government," and said that had he been elected president, he would have ordered searches only when there was probable cause of a crime having been committed, which he said was not how the PRISM program was being operated.[136]
New York Times columnist Thomas L. Friedman defended limited government surveillance programs intended to protect the American people from terrorist acts:
Yes, I worry about potential government abuse of privacy from a program designed to prevent another 9/11—abuse that, so far, does not appear to have happened. But I worry even more about another 9/11. ... If there were another 9/11, I fear that 99 percent of Americans would tell their members of Congress: "Do whatever you need to do to, privacy be damned, just make sure this does not happen again." That is what I fear most. That is why I'll reluctantly, very reluctantly, trade off the government using data mining to look for suspicious patterns in phone numbers called and e-mail addresses—and then have to go to a judge to get a warrant to actually look at the content under guidelines set by Congress—to prevent a day where, out of fear, we give government a license to look at anyone, any e-mail, any phone call, anywhere, anytime.[137]
Political commentator David Brooks similarly cautioned that government data surveillance programs are a necessary evil: "if you don't have mass data sweeps, well, then these agencies are going to want to go back to the old-fashioned eavesdropping, which is a lot more intrusive."[138]
Conservative commentator Charles Krauthammer worried less about the legality of PRISM and other NSA surveillance tools than about the potential for their abuse without more stringent oversight. "The problem here is not constitutionality. ... We need a toughening of both congressional oversight and judicial review, perhaps even some independent outside scrutiny. Plus periodic legislative revision—say, reauthorization every couple of years—in light of the efficacy of the safeguards and the nature of the external threat. The object is not to abolish these vital programs. It's to fix them."[139]
In a blog post, David Simon, the creator of The Wire, compared the NSA's programs, including PRISM, to a 1980s effort by the City of Baltimore to add dialed number recorders to all pay phones to know which individuals were being called by the callers;[140] the city believed that drug traffickers were using pay phones and pagers, and a municipal judge allowed the city to place the recorders. The placement of the dialers formed the basis of the show's first season. Simon argued that the media attention regarding the NSA programs is a "faux scandal."[140][141] Simon had stated that many classes of people in American society had already faced constant government surveillance.
Political theorist, and frequent critic of U.S. government policies, Noam Chomsky argued, "Governments should not have this capacity. But governments will use whatever technology is available to them to combat their primary enemy – which is their own population."[142]
A CNN/Opinion Research Corporation poll conducted June 11 through 13 found that 66% of Americans generally supported the program.[143][144][Notes 1] However, a Quinnipiac University poll conducted June 28 through July 8 found that 45% of registered voters think the surveillance programs have gone too far, with 40% saying they do not go far enough, compared to 25% saying they had gone too far and 63% saying not far enough in 2010.[145] Other polls have shown similar shifts in public opinion as revelations about the programs were leaked.[146][147]
In terms of economic impact, a study released in August by the Information Technology and Innovation Foundation[148] found that the disclosure of PRISM could cost the U.S. economy between $21.5 and $35 billion in lost cloud computing business over three years.[149][150][151][152]
International[edit]
Sentiment around the world was that of general displeasure upon learning the extent of world communication data mining. Some national leaders spoke against the NSA and some spoke against their own national surveillance. One national minister had scathing comments on the National Security Agency's data-mining program, citing Benjamin Franklin: "The more a society monitors, controls, and observes its citizens, the less free it is."[153] Some question if the costs of hunting terrorists now overshadows the loss of citizen privacy.[154][155]
Nick Xenophon, an Australian independent senator, asked Bob Carr, the Australian Minister of Foreign Affairs, if e-mail addresses of Australian parliamentarians were exempt from PRISM, Mainway, Marina, and/or Nucleon. After Carr replied that there was a legal framework to protect Australians but that the government would not comment on intelligence matters, Xenophon argued that this was not a specific answer to his question.[156]
Taliban spokesperson Zabiullah Mujahid said, "We knew about their past efforts to trace our system. We have used our technical resources to foil their efforts and have been able to stop them from succeeding so far."[157][158] However CNN has reported that terrorist groups have changed their "communications behaviors" in response to the leaks.[63]
In 2013 the Cloud Security Alliance surveyed cloud computing stakeholders about their reactions to the US PRISM spying scandal. About 10% of non-US residents indicated that they had cancelled a project with a US-based cloud computing provider, in the wake of PRISM; 56% said that they would be less likely to use a US-based cloud computing service. The Alliance predicted that US cloud computing providers might lose as much as €26 billion and 20% of its share of cloud services in foreign markets because of the PRISM spying scandal.[159]
China and Hong Kong[edit]

Hong Kong rally to support Snowden, June 15, 2013
Reactions of internet users in China were mixed between viewing a loss of freedom worldwide and seeing state surveillance coming out of secrecy. The story broke just before U.S. President Barack Obama and Chinese President Xi Jinping met in California.[160][161] When asked about NSA hacking China, the spokeswoman of Ministry of Foreign Affairs of the People's Republic of China said, "China strongly advocates cybersecurity."[162] The party-owned newspaper Liberation Daily described this surveillance like Nineteen Eighty-Four-style.[163] Hong Kong legislators Gary Fan and Claudia Mo wrote a letter to Obama stating, "the revelations of blanket surveillance of global communications by the world's leading democracy have damaged the image of the U.S. among freedom-loving peoples around the world."[164] Ai Weiwei, a Chinese dissident, said, "Even though we know governments do all kinds of things I was shocked by the information about the US surveillance operation, Prism. To me, it's abusively using government powers to interfere in individuals' privacy. This is an important moment for international society to reconsider and protect individual rights."[165]
Europe[edit]
Sophie in 't Veld, a Dutch Member of the European Parliament, called PRISM "a violation of EU laws."[166]

Digital rights group Digitale Gesellschaft protest at Checkpoint Charlie in Berlin, Germany (June 18, 2013)

Protesters against PRISM in Berlin, Germany wearing Chelsea Manningand Edward Snowden masks (June 19, 2013).
The German Federal Commissioner for Data Protection and Freedom of Information, Peter Schaar, condemned the program as "monstrous."[167] He further added that White House claims do "not reassure me at all" and that "given the large number of German users of Google, Facebook, Apple or Microsoft services, I expect the German government [...] is committed to clarification and limitation of surveillance." Steffen Seibert, press secretary of the Chancellor's office, announced that Angela Merkel will put these issues on the agenda of the talks with Barack Obama during his pending visit in Berlin.[168] Wolfgang Schmidt, a former lieutenant colonel with the Stasi, said that the Stasi would have seen such a program as a "dream come true" since the Stasi lacked the technology that made PRISM possible.[169] Schmidt expressed opposition, saying, "It is the height of naivete to think that once collected this information won't be used. This is the nature of secret government organizations. The only way to protect the people's privacy is not to allow the government to collect their information in the first place."[98] Many Germans organized protests, including one at Checkpoint Charlie, when Obama went to Berlin to speak. Matthew Schofield of the McClatchy Washington Bureau said, "Germans are dismayed at Obama's role in allowing the collection of so much information."[98]
The Italian president of the Guarantor for the protection of personal data, Antonello Soro, said that the surveillance dragnet "would not be legal in Italy" and would be "contrary to the principles of our legislation and would represent a very serious violation."[170]
CNIL (French data protection watchdog) intimates Google to change its privacy policies within three months or it'll risk fines up to 150,000 euros. Spanish Agency of data protection (AEPD) is planning to fine Google between 40k and 300k euros, if it fails to clear about the past usage of the massive data of the Spanish users.[171]
William Hague, the foreign secretary of the United Kingdom, dismissed accusations that British security agencies had been circumventing British law by using information gathered on British citizens by PRISM[172] saying, "Any data obtained by us from the United States involving UK nationals is subject to proper UK statutory controls and safeguards."[172] David Cameron said Britain's spy agencies that received data collected from PRISM acted within the law: "I'm satisfied that we have intelligence agencies that do a fantastically important job for this country to keep us safe, and they operate within the law."[172][173] Malcolm Rifkind, the chairman of parliament's Intelligence and Security Committee, said that if the British intelligence agencies were seeking to know the content of emails about people living in the UK, then they actually have to get lawful authority.[173] The UK's Information Commissioner's Office was more cautious, saying it would investigate PRISM alongside other European data agencies: "There are real issues about the extent to which U.S. law agencies can access personal data of UK and other European citizens. Aspects of U.S. law under which companies can be compelled to provide information to U.S. agencies potentially conflict with European data protection law, including the UK's own Data Protection Act. The ICO has raised this with its European counterparts, and the issue is being considered by the European Commission, who are in discussions with the U.S. Government."[166]
Tim Berners-Lee, the inventor of the World Wide Web, accused western governments of practicing hypocrisy,[174] as they conducted spying on the internet while they criticized other countries for spying on the internet.[175] Berners-Lee said that internet spying can make people feel reluctant to access intimate details or use the internet in a certain way, and as paraphrased by Steve Robson of the Daily Mail, he said that the internet "should be protected from being controlled by governments or large corporations."[174]
India[edit]
Minister of External Affairs Salman Khurshid defended the PRISM program saying, "This is not scrutiny and access to actual messages". It is only computer analysis of patterns of calls and emails that are being sent. It is not actually snooping specifically on content of anybody's message or conversation. Some of the information they got out of their scrutiny, they were able to use it to prevent serious terrorist attacks in several countries."[176] His comments contradicted his Foreign Ministry's characterization of violations of privacy as "unacceptable."[177][178] When Minister of Communications and Information Technology Kapil Sibal was asked about Khurshid's comments, he refused to comment on them directly, but said, "We do not know the nature of data or information sought [as part of PRISM]. Even the external ministry does not have any idea."[179] The media felt that Khurshid's defence of PRISM was because the India government was rolling out the Central Monitoring System (CMS), which is similar to the PRISM program.[180][181][182]
Khurshid's comments were criticized by the Indian media,[183][184] as well as opposition party CPI(M) who stated, "The UPA government should have strongly protested against such surveillance and bugging. Instead, it is shocking that Khurshid has sought to justify it. This shameful remark has come at a time when even the close allies of the US like Germany and France have protested against the snooping on their countries."[185]
Rajya Sabha MP P. Rajeev told The Times of India that "The act of the USA is a clear violation of Vienna convention on diplomatic relations. But Khurshid is trying to justify it. And the speed of the government of India to reject the asylum application of Edward Snowden is shameful."[186]
Legal aspects[edit]
Applicable law and practice[edit]
On June 8, 2013, the Director of National Intelligence issued a fact sheet stating that PRISM "is not an undisclosed collection or data mining program," but rather "an internal government computer system" used to facilitate the collection of foreign intelligence information "under court supervision, as authorized by Section 702 of the Foreign Intelligence Surveillance Act (FISA) (50 U.S.C. § 1881a)."[53] Section 702 provides that "the Attorney General and the Director of National Intelligence may authorize jointly, for a period of up to 1 year from the effective date of the authorization, the targeting of persons reasonably believed to be located outside the United States to acquire foreign intelligence information."[187] In order to authorize the targeting, the Attorney General and Director of National Intelligence need to obtain an order from the Foreign Intelligence Surveillance Court (FISA Court) pursuant to Section 702 or certify that "intelligence important to the national security of the United States may be lost or not timely acquired and time does not permit the issuance of an order."[187] When requesting an order, the Attorney General and Director of National Intelligence must certify to the FISA Court that "a significant purpose of the acquisition is to obtain foreign intelligence information."[187] They do not need to specify which facilities or property will be targeted.[187]
After receiving a FISA Court order or determining that there are emergency circumstances, the Attorney General and Director of National Intelligence can direct an electronic communication service provider to give them access to information or facilities to carry out the targeting and keep the targeting secret.[187] The provider then has the option to: (1) comply with the directive; (2) reject it; or (3) challenge it with the FISA Court. If the provider complies with the directive, it is released from liability to its users for providing the information and is reimbursed for the cost of providing it,[187] while if the provider rejects the directive, the Attorney General may request an order from the FISA Court to enforce it.[187] A provider that fails to comply with the FISA Court's order can be punished with contempt of court.[187]
Finally, a provider can petition the FISA Court to reject the directive.[187] In case the FISA Court denies the petition and orders the provider to comply with the directive, the provider risks contempt of court if it refuses to comply with the FISA Court's order.[187] The provider can appeal the FISA Court's denial to the Foreign Intelligence Surveillance Court of Review and then appeal the Court of Review's decision to the Supreme Court by a writ of certiorari for review under seal.[187]
The Senate Select Committee on Intelligence and the FISA Courts had been put in place to oversee intelligence operations in the period after the death of J. Edgar Hoover. Beverly Gage of Slate said, "When they were created, these new mechanisms were supposed to stop the kinds of abuses that men like Hoover had engineered. Instead, it now looks as if they have come to function as rubber stamps for the expansive ambitions of the intelligence community. J. Edgar Hoover no longer rules Washington, but it turns out we didn't need him anyway."[188]
Litigation[edit]
June 11, 2013 American Civil Liberties Union Lawsuit filed against the NSA citing that the "Mass Call Tracking Program" (as the case terms PRISM) "violates Americans' constitutional rights of free speech, association, and privacy" and constitutes "dragnet" surveillance, in violation of the First and Fourth Amendments to the Constitution, and thereby also "exceeds the authority granted by 50 U.S.C. § 1861, and thereby violates 5 U.S.C. § 706."[189] The case was joined by Yale Law School, on behalf of its Media Freedom and Information Access Clinic.[190]
June 11, 2013 FreedomWatch USA Class action lawsuit against government bodies and officials believed responsible for PRISM, and 12 companies (including Apple, Microsoft, Google, Facebook, and Skype and their chief executives) who have been disclosed as providing or making available mass information about their users' communications and data to the NSA under the PRISM program or related programs. The case cites the First, Fourth, and Fifth Amendments to the Constitution, as well as breach of 18 U.S.C. §§2702 (disclosure of communications records), and asks the court to rule that the program operates outside its legal authority (s.215 of the Patriot Act). The class includes the plaintiffs and[191]"other American citizens who, in addition to being members of the Nationwide Class, had their telephone calls and/or emails and/or any other communications made or received through Facebook, Google, Yahoo, YouTube, Skype, AOL, Sprint, AT&T, Apple, Microsoft and/or PalTalk actually recorded and/or listened into by or on behalf of [the] Defendants."
In November 2017, the district court dismissed the case.
February 18, 2014 Rand Paul and Freedom Works, Inc. Lawsuit filed against President Barack Obama, James R. Clapper, as Director of National Intelligence, Keith B. Alexander, as Director of the NSA, James B. Comey, as Director of the FBI, in the United States District Court for the District of Columbia. The case contends that the Defendants are violating the Fourth Amendment of the United States by collecting phone metadata. The case is currently stayed pending the outcome of the government's appeal in the Klayman case.
June 2, 2014 Elliott J. Schuchardt Lawsuit filed against President Barack Obama, James R. Clapper, as Director of National Intelligence, Admiral Michael R. Rogers, as Director of the NSA, James B. Comey, as Director of the FBI, in the United States District Court for the Western District of Pennsylvania. The case contends that the Defendants are violating the Fourth Amendment of the United States by collecting the full content of e-mail in the United States. The complaint asks the Court to find the Defendants' program unconstitutional, and seeks an injunction. The court is currently considering the government's motion to dismiss this case.
Analysis of legal issues[edit]
Laura Donohue, a law professor at the Georgetown University Law Center and its Center on National Security and the Law, has called PRISM and other NSA mass surveillance programs unconstitutional.[192]
Woodrow Hartzog, an affiliate at Stanford Law School's Center for Internet and Society commented that "[The ACLU will] likely have to demonstrate legitimate First Amendment harms (such as chilling effects) or Fourth Amendment harms (perhaps a violation of a reasonable expectation of privacy)... Is it a harm to merely know with certainty that you are being monitored by the government? There's certainly an argument that it is. People under surveillance act differently, experience a loss of autonomy, are less likely to engage in self exploration and reflection, and are less willing to engage in core expressive political activities such as dissenting speech and government criticism. Such interests are what First and Fourth Amendment seek to protect."[193]
Legality of the FISA Amendments Act[edit]
The FISA Amendments Act (FAA) Section 702 is referenced in PRISM documents detailing the electronic interception, capture and analysis of metadata. Many reports and letters of concern written by members of Congress suggest that this section of FAA in particular is legally and constitutionally problematic, such as by targeting U.S. persons, insofar as "Collections occur in U.S." as published documents indicate.[194][195][196][197]
The ACLU has asserted the following regarding the FAA: "Regardless of abuses, the problem with the FAA is more fundamental: the statute itself is unconstitutional."[198]
Senator Rand Paul is introducing new legislation called the Fourth Amendment Restoration Act of 2013 to stop the NSA or other agencies of the United States government from violating the Fourth Amendmentto the U.S. Constitution using technology and big data information systems like PRISM and Boundless Informant.[199][200]
Programs sharing the name PRISM[edit]
Besides the information collection program started in 2007, there are two other programs sharing the name PRISM:[201]
The Planning tool for Resource Integration, Synchronization and Management (PRISM), a web tool used by US military intelligence to send tasks and instructions to data collection platforms deployed to military operations.[202]
The Portal for Real-time Information Sharing and Management (PRISM), whose existence was revealed by the NSA in July 2013.[201] This is an internal NSA program for real-time sharing of information which is apparently located in the NSA's Information Assurance Directorate.[201] The NSA's Information Assurance Directorate (IAD) is a very secretive division which is responsible for safeguarding U.S. government and military secrets by implementing sophisticated encryption techniques.[201]
Related NSA programs[edit]
Main article: List of government mass surveillance projects
Parallel programs, known collectively as SIGADs gather data and metadata from other sources, each SIGAD has a set of defined sources, targets, types of data collected, legal authorities, and software associated with it. Some SIGADs have the same name as the umbrella under which they sit, BLARNEY's (the SIGAD) summary, set down in the slides alongside a cartoon insignia of a shamrock and a leprechaun hat, describes it as "an ongoing collection program that leverages IC [intelligence community] and commercial partnerships to gain access and exploit foreign intelligence obtained from global networks."
Some SIGADs, like PRISM, collect data at the ISP level, but others take it from the top-level infrastructure. This type of collection is known as "upstream". Upstream collection includes programs known by the blanket terms BLARNEY, FAIRVIEW, OAKSTAR and STORMBREW, under each of these are individual SIGADs. Data that is integrated into a SIGAD can be gathered in other ways besides upstream, and from the service providers, for instance it can be collected from passive sensors around embassies, or even stolen from an individual computer network in a hacking attack.[203][204][205][206][207] Not all SIGADs involve upstream collection, for instance, data could be taken directly from a service provider, either by agreement (as is the case with PRISM), by means of hacking, or other ways.[208][209][210]
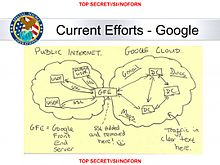
Idea behind the MUSCULARprogram, which gave direct access to Google and Yahoo private clouds, no warrants needed
According to the Washington Post, the much less known MUSCULAR program, which directly taps the unencrypted data inside the Google and Yahoo private clouds, collects more than twice as many data points compared to PRISM.[211] Because the Google and Yahoo clouds span the globe, and because the tap was done outside of the United States, unlike PRISM, the MUSCULAR program requires no (FISA or other type of) warrants.[212
XKeyscore or XKEYSCORE (abbreviated as XKS) is a formerly secret computer system first used by the United States National Security Agency for searching and analyzing global Internet data, which it collects on a daily basis. The program has been shared with other spy agencies including the Australian Signals Directorate, Canada's Communications Security Establishment, New Zealand's Government Communications Security Bureau, Britain's Government Communications Headquarters and the German Bundesnachrichtendienst.[1]
The program's purpose was publicly revealed in July 2013, by Edward Snowden in The Sydney Morning Herald and O Globo newspapers. The code name was already public knowledge because it is mentioned in earlier articles, and like many other code names can also be seen in job postings, and in the online resumes of employees.[2][3]
On July 3, 2014, excerpts of XKeyscore's source code were first published by German public broadcaster Norddeutscher Rundfunk, a member of ARD.[4] A team of experts analyzed the source code
Contents [hide]
1Scope and functioning
1.1According to Snowden and Greenwald
1.2According to the NSA
2Workings
2.1Data sources
2.2Types of XKeyscore
2.3Capabilities
3Contribution to U.S. security
4Usage by foreign partners of the NSA
4.1Germany
4.2Sweden
4.3Japan
5Gallery
6See also
7References
8External links
Scope and functioning[edit]
XKeyscore is a complicated system, and various authors have different interpretations of its actual capabilities. Edward Snowden and Glenn Greenwald explained XKeyscore as being a system which enables almost unlimited surveillance of anyone anywhere in the world, while the NSA has said that usage of the system is limited and restricted.
According to The Washington Post and national security reporter Marc Ambinder, XKeyscore is an NSA data-retrieval system which consists of a series of user interfaces, backend databases, servers and software that selects certain types of data and metadata that the NSA has already collected using other methods.[6][7]
According to Snowden and Greenwald[edit]
On January 26, 2014, the German broadcaster Norddeutscher Rundfunk asked Edward Snowden in its TV interview: "What could you do if you would [sic] use XKeyscore?" and he answered:[1]
You could read anyone's email in the world, anybody you've got an email address for. Any website: You can watch traffic to and from it. Any computer that an individual sits at: You can watch it. Any laptop that you're tracking: you can follow it as it moves from place to place throughout the world. It's a one-stop-shop for access to the NSA's information.
…You can tag individuals… Let's say you work at a major German corporation and I want access to that network, I can track your username on a website on a form somewhere, I can track your real name, I can track associations with your friends and I can build what's called a fingerprint, which is network activity unique to you, which means anywhere you go in the world, anywhere you try to sort of hide your online presence, your identity.
According to The Guardian's Glenn Greenwald, low-level NSA analysts can, via systems like XKeyscore, "listen to whatever emails they want, whatever telephone calls, browsing histories, Microsoft Word documents. And it's all done with no need to go to a court, with no need to even get supervisor approval on the part of the analyst."[8]
He added that the NSA's databank of collected communications allows its analysts to listen "to the calls or read the emails of everything that the NSA has stored, or look at the browsing histories or Google search terms that you've entered, and it also alerts them to any further activity that people connected to that email address or that IP address do in the future".[8]
According to the NSA[edit]
Further information: SIGINT
In an official statement from July 30, 2013, the NSA said "XKeyscore is used as a part of NSA's lawful foreign signals intelligence collection system. [...]" to legally obtain information about "legitimate foreign intelligence targets in response to requirements that our leaders need for information necessary to protect our nation and its interests. [...] to collect the information, that enables us to perform our missions successfully – to defend the nation and to protect U.S. and allied troops abroad."[9] In terms of access, an NSA press statement reads that there is no "unchecked analyst access to NSA collection data. Access to XKeyscore, as well as all of NSA's analytic tools, is limited to only those personnel who require access for their assigned tasks." and that there are "[...]stringent oversight and compliance mechanisms built in at several levels. One feature is the system's ability to limit what an analyst can do with a tool, based on the source of the collection and each analyst's defined responsibilities."[10]
Workings[edit]

Slide from a 2008 NSA presentation about XKeyscore, showing a worldmap with the locations of XKeyscore servers
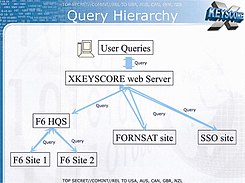
Slide from a 2008 NSA presentation about XKeyscore, showing the query hierarchy
According to an NSA slide presentation about XKeyscore from 2013, it is a "DNI Exploitation System/Analytic Framework". DNI stands for Digital Network Intelligence, which means intelligence derived from internet traffic.[11]
Edward Snowden said about XKeyscore: "It’s a front end search engine" in an interview with the German Norddeutscher Rundfunk.[12]
XKeyscore is considered a "passive" program, in that it listens, but does not transmit anything on the networks that it targets.[5] But it can trigger other systems, which perform "active" attacks through Tailored Access Operations which are "tipping", for example, the QUANTUM family of programs, including QUANTUMINSERT, QUANTUMHAND, QUANTUMTHEORY, QUANTUMBOT and QUANTUMCOPPER and Turbulence. These run at so-called "defensive sites" including the Ramstein Air Force base in Germany, Yokota Air Base in Japan, and numerous military and non-military locations within the US. Trafficthief, a core program of Turbulence, can alert NSA analysts when their targets communicate, and trigger other software programs, so select data is "promoted" from the local XKeyscore data store to the NSA's "corporate repositories" for long term storage.[5]
Data sources[edit]
XKeyscore consists of over 700 servers at approximately 150 sites where the NSA collects data, like "US and allied military and other facilities as well as US embassies and consulates" in many countries around the world.[13][14][15] Among the facilities involved in the program are four bases in Australia and one in New Zealand.[14]
According to an NSA presentation from 2008, these XKeyscore servers are fed with data from the following collection systems:[16]
F6 (Special Collection Service) – joint operation of the CIA and NSA that carries out clandestine operations including espionage on foreign diplomats and leaders
FORNSAT – which stands for "foreign satellite collection", and refers to intercepts from satellites
SSO (Special Source Operations) – a division of the NSA that cooperates with telecommunication providers
In a single, undated slide published by Swedish media in December 2013, the following additional data sources for XKeyscore are mentioned:[17]
Overhead – intelligence derived from American spy planes, drones and satellites
Tailored Access Operations – a division of the NSA that deals with hacking and cyberwarfare
FISA – all types of surveillance approved by the Foreign Intelligence Surveillance Court
Third party – foreign partners of the NSA such as the (signals) intelligence agencies of Belgium, Denmark, France, Germany, Italy, Japan, the Netherlands, Norway, Sweden, etc.
From these sources, XKeyscore stores "full-take data", which are indexed by plug-ins that extract certain types of metadata (like phone numbers, e-mail addresses, log-ins, and user activity) and index them in metadata tables, which can be queried by analysts. XKeyscore has been integrated with MARINA, which is NSA's database for internet metadata.[11]
However, the system continuously gets so much Internet data that it can be stored only for short periods of time. Content data remain on the system for only three to five days, while metadata is stored for up to thirty days.[18] A detailed commentary on an NSA presentation published in The Guardian in July 2013 cites a document published in 2008 declaring that "At some sites, the amount of data we receive per day (20+ terabytes) can only be stored for as little as 24 hours."[19]
Types of XKeyscore[edit]
According to a document from an internal GCHQ website which was disclosed by the German magazine Der Spiegel in June 2014, there are three different types of the Xkeyscore system:[20]
Traditional: The initial version of XKeyscore is fed with data from low-rate data signals, after being processed by the WEALTHYCLUSTER system. This traditional version is not only used by NSA but also at many intercept sites of GCHQ.
Stage 2: This version of XKeyscore is used for higher data rates. The data are first processed by the TURMOIL system, which sends 5% of the internet data packets to XKeyscore. GCHQ only uses this version for its collection under the MUSCULAR program.
Deep Dive: This latest version can process internet traffic at data rates of 10 gigabits per second. Data that could be useful for intelligence purposes are then selected and forwarded by using the "GENESIS selection language". GCHQ also operates a number of Deep Dive versions of XKeyscore at three locations under the codename TEMPORA.[21]
Capabilities[edit]

Slide from a 2008 NSA presentation about XKeyscore, showing the differences between the various NSA database systems
For analysts, XKeyscore provides a "series of viewers for common data types", which allows them to query terabytes of raw data gathered at the aforementioned collection sites. This enables them to find targets that cannot be found by searching only the metadata, and also to do this against data sets that otherwise would have been dropped by the front-end data processing systems. According to a slide from an XKeyscore presentation, NSA collection sites select and forward less than 5% of the internet traffic to the PINWALE database for internet content.[18]
Because XKeyscore holds raw and unselected communications traffic, analysts can not only perform queries using "strong selectors" like e-mail addresses, but also using "soft selectors", like keywords, against the body texts of e-mail and chat messages and digital documents and spreadsheets in English, Arabic and Chinese.[11]
This is useful because "a large amount of time spent on the web is performing actions that are anonymous" and therefore those activities can't be found by just looking for e-mail addresses of a target. When content has been found, the analyst might be able to find new intelligence or a strong selector, which can then be used for starting a traditional search.[11]
Besides using soft selectors, analysts can also use the following other XKeyscore capabilities:[11][22]
Look for the usage of Google Maps and terms entered into a search engine by known targets looking for suspicious things or places.
Look for "anomalies" without any specific person attached, like detecting the nationality of foreigners by analyzing the language used within intercepted emails. An example would be a German speaker in Pakistan. The Brazilian paper O Globo claims that this has been applied to Latin America and specifically to Colombia, Ecuador, Mexico and Venezuela.[13][23]
Detect people who use encryption by doing searches like "all PGP usage in Iran". The caveat given is that very broad queries can result in too much data to transmit back to the analyst.
Showing the usage of virtual private networks (VPNs) and machines that can potentially be hacked via TAO.
Track the source and authorship of a document that has passed through many hands.
On July 3, 2014 ARD revealed that XKeyscore is used to closely monitor users of the Tor anonymity network,[5] people who search for privacy-enhancing software on the web,[5] and readers of Linux Journal.[24]
The Guardian opined in 2013 that most of these things cannot be detected by other NSA tools, because they operate with strong selectors (like e-mail and IP addresses and phone numbers) and the raw data volumes are too high to be forwarded to other NSA databases.[11]
In 2008, NSA planned to add a number of new capabilities in the future, like VoIP, more networking protocols[clarify], Exif tags, which often include geolocation (GPS) data.[11]
Contribution to U.S. security[edit]
The NSA slides published in The Guardian during 2013 claimed that XKeyscore had played a role in capturing 300 terrorists by 2008,[11] which could not be substantiated as the redacted documents do not cite instances of terrorist interventions.
A 2011 report from the NSA unit in the Dagger Complex (close to Griesheim in Germany) said that XKeyscore made it easier and more efficient to target surveillance. Previously, analysis often accessed data NSA was not interested in. XKeyscore allowed them to focus on the intended topics, while ignoring unrelated data. XKeyscore also proved to be outstanding for tracking active groups associated with the Anonymous movement in Germany, because it allows for searching on patterns, rather than particular individuals. An analyst is able to determine when targets research new topics, or develop new behaviors.[25]
To create additional motivation, the NSA incorporated various gamification features. For instance, analysts who were especially good at using XKeyscore could acquire "skilz" points and "unlock achievements." The training units in Griesheim were apparently successful and analysts there had achieved the "highest average of skilz points" compared with all other NSA departments participating in the training program.[25]
Usage by foreign partners of the NSA[edit]
Germany[edit]

Excerpt of an NSA document leaked by Edward Snowden that reveals the BND's usage of the NSA's XKeyscore to wiretap a German domestic target
According to documents Der Spiegel acquired from Snowden, the German intelligence agencies BND (foreign intelligence) and BfV (domestic intelligence) were also allowed to use the XKeyscore system. In those documents the BND agency was described as the NSA's most prolific partner in information gathering.[26] This led to political confrontations, after which the directors of the German intelligence agencies briefed members of the German parliamentary intelligence oversight committee on July 25, 2013. They declared that XKeyscore has been used by the BND since 2007 and that the BfV uses a test version since 2012. The directors also explained that this program is not for collecting data, but only for analyzing them.[27]
Sweden[edit]
As part of the UKUSA Agreement, a secret treaty was signed in 1954 by Sweden with the United States, the United Kingdom, Canada, Australia and New Zealand (called the Five Eyes) for the purpose of intelligence collaboration and data sharing.[28] According to documents leaked by Snowden, the National Defence Radio Establishment (FRA) has been granted access to XKeyscore.[29]
Japan[edit]
The classified documents leaked by Snowden also indicate that in April 2013, NSA had secretly provided the XKeyscore system to the Japanese government.[30]
ECHELON, originally a secret government code name, is a surveillance program (signals intelligence/SIGINT collection and analysis network) operated by the US with the aid of four other signatory nations to the UKUSA Security Agreement[1]: Australia, Canada, New Zealand, the United Kingdom and the United States, also known as the Five Eyes.[2][3][4]
The ECHELON program was created in the late 1960s to monitor the military and diplomatic communications of the Soviet Union and its Eastern Bloc allies during the Cold War, and was formally established in 1971.[5][6]
By the end of the 20th century, the system referred to as "ECHELON" had allegedly evolved beyond its military and diplomatic origins, to also become "…a global system for the interception of private and commercial communications" (mass surveillance and industrial espionage
Contents
[hide]
1Name
2Reporting and disclosures
2.1Public disclosures (1972–2000)
2.2European Parliament investigation (2000–2001)
2.3Confirmation of ECHELON (2015)
3Organization
3.1Likely satellite intercept stations
3.2Other potentially related stations
4History and context
5Concerns
6Workings
7In popular culture
8See also
9Bibliography
10Notes and references
11External links
Name[edit]
The European Parliament's Temporary Committee on the ECHELON Interception System stated, "It seems likely, in view of the evidence and the consistent pattern of statements from a very wide range of individuals and organisations, including American sources, that its name is in fact ECHELON, although this is a relatively minor detail".[7] The U.S. intelligence community uses many code names (see, for example, CIA cryptonym).
Former NSA employee Margaret Newsham claims that she worked on the configuration and installation of software that makes up the ECHELON system while employed at Lockheed Martin, from 1974 to 1984 in Sunnyvale, California, in the United States, and in Menwith Hill, England, in the UK.[8] At that time, according to Newsham, the code name ECHELON was NSA's term for the computer network itself. Lockheed called it P415. The software programs were called SILKWORTHand SIRE. A satellite named VORTEX intercepted communications. An image available on the internet of a fragment apparently torn from a job description shows Echelon listed along with several other code names.[9][10]
Britain's The Guardian newspaper summarized the capabilities of the ECHELON system as follows:
A global network of electronic spy stations that can eavesdrop on telephones, faxes and computers. It can even track bank accounts. This information is stored in Echelon computers, which can keep millions of records on individuals.
Officially, however, Echelon doesn't exist.[11]
Reporting and disclosures[edit]
Public disclosures (1972–2000)[edit]
In 1972, former NSA analyst Perry Fellwock under pseudonym Winslow Peck, first blew the whistle on ECHELON to Ramparts in 1972,[12] where he gave commentary revealing a global network of listening posts and his experiences working there. Fellwock also included revelations such as the Israeli attack on USS Liberty was deliberate and known by both sides, the existence of nuclear weapons in Israel in 1972, the widespread involvement of CIA and NSA personnel in drugs and human smuggling, and CIA operatives leading Nationalist China (Taiwan) commandos in burning villages inside PRC borders.[13]
In 1982, James Bamford, investigative journalist and author wrote The Puzzle Palace, an in-depth look inside the workings of the NSA, then a super-secret agency, and the massive eavesdropping operation under the codename "SHAMROCK". The NSA has used many codenames, and SHAMROCK was the codename used for ECHELON prior to 1975.[14][15]
In 1988, Margaret Newsham, a Lockheed employee under NSA contract, disclosed the ECHELON surveillance system to members of congress. Newsham told a member of the U.S. Congress that the telephone calls of Strom Thurmond, a Republican U.S. senator, were being collected by the NSA. Congressional investigators determined that "targeting of U.S. political figures would not occur by accident, but was designed into the system from the start."[16]
Also in 1988, an article titled "Somebody's Listening", written by investigative journalist Duncan Campbell in the New Statesman, described the signals intelligence gathering activities of a program code-named "ECHELON".[16] James Bamford describes the system as the software controlling the collection and distribution of civilian telecommunications traffic conveyed using communication satellites, with the collection being undertaken by ground stations located in the footprint of the downlink leg.[17]
In 1996, a detailed description of ECHELON was provided by New Zealand journalist Nicky Hager in his 1996 book Secret Power: New Zealand's Role in the International Spy Network.[18] Two years later, Hager's book was cited by the European Parliament in a report titled "An Appraisal of the Technology of Political Control" (PE 168.184).[19]
In March 1999, for the first time in history, the Australian government admitted that news reports about the top secret UKUSA Agreement were true.[20] Martin Brady, the director of Australia's Defence Signals Directorate (DSD) told the Australian broadcasting channel Nine Network that the DSD "does co-operate with counterpart signals intelligence organisations overseas under the UKUSA relationship."[21]
In 2000, James Woolsey, the former Director of the U.S. Central Intelligence Agency, confirmed that U.S. intelligence uses interception systems and keyword searches to monitor European businesses.[22]
Lawmakers in the United States feared that the ECHELON system could be used to monitor U.S. citizens.[23] According to The New York Times, the ECHELON system has been "shrouded in such secrecy that its very existence has been difficult to prove."[23] Critics said the ECHELON system emerged from the Cold War as a "Big Brother without a cause".[24]
European Parliament investigation (2000–2001)[edit]

The New Zealand journalist Nicky Hager, who testified before the European Parliament and provided specific details about the ECHELON surveillance system[25]
The program's capabilities and political implications were investigated by a committee of the European Parliament during 2000 and 2001 with a report published in 2001.[7] In July 2000, the Temporary Committee on the ECHELON Interception System was established by the European parliament to investigate the surveillance network. It was chaired by the Portuguese politician Carlos Coelho, who was in charge of supervising investigations throughout 2000 and 2001.
In May 2001, as the committee finalised its report on the ECHELON system, a delegation travelled to Washington, D.C. to attend meetings with U.S. officials from the following agencies and departments:
U.S. Central Intelligence Agency (CIA)[26]
U.S. Department of Commerce (DOC)[26]
U.S. National Security Agency (NSA)[26]
All meetings were cancelled by the U.S. government and the committee was forced to end its trip prematurely.[26] According to a BBC correspondent in May 2001, "The US Government still refuses to admit that Echelon even exists."[5]
In July 2001, the Temporary Committee on the ECHELON Interception System released its final report.[27] On 5 September 2001, the European Parliament voted to accept the committee's report.[28]
The European Parliament stated in its report that the term ECHELON is used in a number of contexts, but that the evidence presented indicates that it was the name for a signals intelligence collection system. The report concludes that, on the basis of information presented, ECHELON was capable of interception and content inspection of telephone calls, fax, e-mail and other data traffic globally through the interception of communication bearers including satellite transmission, public switched telephone networks (which once carried most Internet traffic), and microwave links.[7]
Confirmation of ECHELON (2015)[edit]
Two internal NSA newsletters from January 2011 and July 2012, published as part of the Snowden-revelations by the website The Intercept on 3 August 2015, for the first time confirmed that NSA used the codeword ECHELON and provided some details about the scope of the program: ECHELON was part of an umbrella program codenamed FROSTING, which was established by the NSA in 1966 to collect and process data from communications satellites. FROSTING had two sub-programs:[29]
TRANSIENT: for intercepting Soviet satellite transmissions, and
ECHELON: for intercepting Intelsat satellite transmissions.
Organization[edit]
UKUSA Community
 AustraliaCanadaNew ZealandUnited KingdomUnited States
AustraliaCanadaNew ZealandUnited KingdomUnited StatesThe UKUSA intelligence community was assessed by the European Parliament (EP) in 2000 to include the signals intelligence agencies of each of the member states:
the Government Communications Headquarters of the United Kingdom,
the National Security Agency of the United States,
the Communications Security Establishment of Canada,
the Australian Signals Directorate of Australia, and
the Government Communications Security Bureau of New Zealand.
The EP report concluded that it seemed likely that ECHELON is a method of sorting captured signal traffic, rather than a comprehensive analysis tool.[7]
Likely satellite intercept stations[edit]
In 2001, the EP report (p. 54 ff)[7] listed the following ground stations as likely to have, or to have had, a role in intercepting transmissions from telecommunications satellites:
Hong Kong (since closed)
Australian Defence Satellite Communications Station (Geraldton, Western Australia)
RAF Menwith Hill (Yorkshire, U.K.) Map (reportedly the largest Echelon facility)[30]
Misawa Air Base (Japan) Map
GCHQ Bude, formerly known as GCHQ CSO Morwenstow (Cornwall, U.K.) Map
Pine Gap (Northern Territory, Australia – close to Alice Springs) Map
Sugar Grove (West Virginia, U.S.) Map (since closed)
Yakima Training Center (Washington, U.S.) Map (since closed)
GCSB Waihopai (New Zealand)[31]
GCSB Tangimoana (New Zealand)[31]
CFS Leitrim (Ontario, Canada)[32]
Teufelsberg (Berlin, Germany) (closed 1992)[33] – Responsible for listening in to the Eastern Bloc.[34]
Other potentially related stations[edit]
The following stations are listed in the EP report (p. 57 ff) as ones whose roles "cannot be clearly established":
Ayios Nikolaos (British Sovereign Base area of Dhekelia, Cyprus – U.K.)
Gibraltar (U.K.)
Diego Garcia (U.K.)
Bad Aibling Station (Bad Aibling, Germany – U.S.)
relocated to Griesheim/Darmstadt in 2004.[35]
Buckley Air Force Base (Aurora, Colorado)
Fort Gordon (Georgia, U.S.)
CFB Gander (Newfoundland & Labrador, Canada)[citation needed]
Guam (Pacific Ocean, U.S.)
Kunia Regional SIGINT Operations Center (Hawaii, U.S.)
Lackland Air Force Base, Medina Annex (San Antonio, Texas)
RAF Edzell (Scotland)[citation needed]
RAF Boulmer (England)[citation needed]
List of intercept stations according to Edward Snowden's documentsOperated by the United States
CountryLocationOperator(s)Codename
 Brazil Brasília, Federal District
Brazil Brasília, Federal District  CIA[36]
CIA[36] NSA[36] SCS
NSA[36] SCS Germany Bad Aibling, Munich
Germany Bad Aibling, Munich  BND[37]
BND[37] NSA[37] GARLICK[38]
NSA[37] GARLICK[38] India New Delhi
India New Delhi  CIA[39]
CIA[39] NSA[39] SCS
NSA[39] SCS Japan Misawa, Tōhoku region
Japan Misawa, Tōhoku region  US Air Force[40]
US Air Force[40] NSA[40] LADYLOVE[41]
NSA[40] LADYLOVE[41] Thailand Bangkok (?)
Thailand Bangkok (?)  CIA (?)
CIA (?) NSA (?) LEMONWOOD[42]
NSA (?) LEMONWOOD[42] United Kingdom Menwith Hill, Harrogate
United Kingdom Menwith Hill, Harrogate  NSA[43]*
NSA[43]*  GCHQ MOONPENNY[42]
GCHQ MOONPENNY[42] United States Sugar Grove, West Virginia
United States Sugar Grove, West Virginia  NSA[44] TIMBERLINE[45]
NSA[44] TIMBERLINE[45]Yakima, Washington
 NSA[46] JACKKNIFE[42]
NSA[46] JACKKNIFE[42]Sábana Seca, Puerto Rico
 NSA[47] CORALINE[42]
NSA[47] CORALINE[42]Not operated by the United States (2nd party)
CountryLocationContributor(s)Codename
 Australia Geraldton, WA
Australia Geraldton, WA  ASD[40] STELLAR[40]
ASD[40] STELLAR[40]Darwin, NT
 ASD[40] ?[40]
ASD[40] ?[40] New Zealand Waihopai, Blenheim
New Zealand Waihopai, Blenheim  GCSB[40] IRONSAND[40]
GCSB[40] IRONSAND[40] United Kingdom Bude, Cornwall
United Kingdom Bude, Cornwall  GCHQ[48]
GCHQ[48] NSA[48] CARBOY[45]
NSA[48] CARBOY[45] Cyprus Ayios Nikolaos Station
Cyprus Ayios Nikolaos Station  GCHQ[48]
GCHQ[48] NSA[48] SOUNDER[49]
NSA[48] SOUNDER[49] Kenya Nairobi
Kenya Nairobi  GCHQ[40] SCAPEL[42]
GCHQ[40] SCAPEL[42] Oman
Oman  GCHQ[40] SNICK[42]
GCHQ[40] SNICK[42]History and context[edit]
The ability to intercept communications depends on the medium used, be it radio, satellite, microwave, cellular or fiber-optic.[7] During World War II and through the 1950s, high-frequency ("short-wave") radio was widely used for military and diplomatic communication[50] and could be intercepted at great distances.[7] The rise of geostationary communications satellites in the 1960s presented new possibilities for intercepting international communications.
In 1964, plans for the establishment of the ECHELON network took off after dozens of countries agreed to establish the International Telecommunications Satellite Organisation (Intelsat), which would own and operate a global constellation of communications satellites.[20]

Equipment at the Yakima Research Station (YRS) in the early days of the ECHELON program

Teletype operators at the Yakima Research Station (YRS) in the early days of the ECHELON program
In 1966, the first Intelsat satellite was launched into orbit. From 1970 to 1971, the Government Communications Headquarters (GCHQ) of Britain began to operate a secret signal station at Morwenstow, near Bude in Cornwall, England. The station intercepted satellite communications over the Atlantic and Indian Oceans. Soon afterwards, the U.S. National Security Agency (NSA) built a second signal station at Yakima, near Seattle, for the interception of satellite communications over the Pacific Ocean.[20]
In 1981, the GCHQ and the NSA started the construction of the first global wide area network (WAN). Soon after Australia, Canada, and New Zealand joined the ECHELON system.[20] The report to the European Parliament of 2001 states: "If UKUSA states operate listening stations in the relevant regions of the earth, in principle they can intercept all telephone, fax, and data traffic transmitted via such satellites."[7]
Most reports on ECHELON focus on satellite interception. Testimony before the European Parliament indicated that separate but similar UK-U.S. systems are in place to monitor communication through undersea cables, microwave transmissions, and other lines.[51] The report to the European Parliament points out that interception of private communications by foreign intelligence services is not necessarily limited to the U.S. or British foreign intelligence services.[7]
The role of satellites in point-to-point voice and data communications has largely been supplanted by fiber optics. In 2006, 99% of the world's long-distance voice and data traffic was carried over optical-fiber.[52] The proportion of international communications accounted for by satellite links is said to have decreased substantially to an amount between 0.4% and 5% in Central Europe.[7] Even in less-developed parts of the world, communications satellites are used largely for point-to-multipoint applications, such as video.[53] Thus, the majority of communications can no longer be intercepted by earth stations; they can only be collected by tapping cables and intercepting line-of-sight microwave signals, which is possible only to a limited extent.[7]
Concerns[edit]
British journalist Duncan Campbell and New Zealand journalist Nicky Hager asserted in the 1990s that the United States was exploiting ECHELON traffic for industrial espionage, rather than military and diplomatic purposes.[51] Examples alleged by the journalists include the gear-less wind turbine technology designed by the German firm Enercon[7][54] and the speech technology developed by the Belgian firm Lernout & Hauspie.[55]
In 2001, the Temporary Committee on the ECHELON Interception System recommended to the European Parliament that citizens of member states routinely use cryptography in their communications to protect their privacy, because economic espionage with ECHELON has been conducted by the U.S. intelligence agencies.[7]
American author James Bamford provides an alternative view, highlighting that legislation prohibits the use of intercepted communications for commercial purposes, although he does not elaborate on how intercepted communications are used as part of an all-source intelligence process.
In its report, the committee of the European Parliament stated categorically that the Echelon network was being used to intercept not only military communications, but also private and business ones. In its epigraph to the report, the parliamentary committee quoted Juvenal, "Sed quis custodiet ipsos custodes." ("But who will watch the watchers").[7] James Bamford, in The Guardian in May 2001, warned that if Echelon were to continue unchecked, it could become a "cyber secret police, without courts, juries, or the right to a defence".[56]
Alleged examples of espionage conducted by the members of the "Five Eyes" include:
On behalf of the British Prime Minister Margaret Thatcher, the Canadian Security Intelligence Service of Canada spied on two British cabinet ministers in 1983.[57]
The U.S. National Security Agency spied on and intercepted the phone calls of Princess Diana right until she died in a Paris car crash with Dodi Fayed in 1997. The NSA currently holds 1,056 pages of classified information about Princess Diana, which has been classified as top secret "because their disclosure could reasonably be expected to cause exceptionally grave damage to the national security ... the damage would be caused not by the information about Diana, but because the documents would disclose 'sources and methods' of U.S. intelligence gathering".[58] An official insisted that "the references to Diana in intercepted conversations were 'incidental'," and she was never a 'target' of the NSA eavesdropping.[58]
U.K. agents monitored the conversations of the 7th Secretary-General of the United Nations Kofi Annan.[59][60]
U.S. agents gathered "detailed biometric information" on the 8th Secretary-General of the United Nations, Ban Ki-Moon.[61][62]
In the early 1990s, the U.S. National Security Agency intercepted the communications between the European aerospace company Airbus and the Saudi Arabian national airline. In 1994, Airbus lost a $6 billion contract with Saudi Arabia after the NSA, acting as a whistleblower, reported that Airbus officials had been bribing Saudi officials to secure the contract.[63] As a result, the American aerospace company McDonnell Douglas (now part of Boeing) won the multibillion-dollar contract instead of Airbus.[64]
The American defense contractor Raytheon won a US$1.3 billion contract with the Government of Brazil to monitor the Amazon rainforest after the U.S. Central Intelligence Agency (CIA), acting as a whistleblower, reported that Raytheon's French competitor Thomson-Alcatel had been paying bribes to get the contract.[65]
In order to boost America's position in trade negotiations with the then Japanese Trade Minister Ryutaro Hashimoto, in 1995 the CIA eavesdropped on the conversations between Japanese bureaucrats and executives of car manufacturers Toyota and Nissan.[66]
Workings[edit]

System diagram of the ECHELON satellite intercept station of the NSA at the Yakima Research Station (YRS) [67]
TOPCO = Terminal Operations Control
CCS = Computer Control Subsystem
STEAMS = System Test, Evaluation, Analysis, and Monitoring Subsystem
SPS = Signal Processing Subsystem
TTDM = Teletype Demodulator
The first American satellite ground station for the ECHELON collection program was built in 1971 at a military firing and training center near Yakima, Washington. The facility, which was codenamed JACKKNIFE, was an investment of ca. 21.3 million dollars and had around 90 people. Satellite traffic was intercepted by a 30-meter single dish antenna. The station became fully operational on 4 October 1974. It was connected with NSA headquarters at Fort Meade by a 75-baud secure Teletype orderwire channel.[29]
In 1999 the Australian Senate Joint Standing Committee on Treaties was told by Professor Desmond Ball that the Pine Gap facility was used as a ground station for a satellite-based interception network. The satellites were said to be large radio dishes between 20 and 100 meters in diameter in geostationary orbits. The original purpose of the network was to monitor the telemetry from 1970s Soviet weapons, air defence- and other radar's capabilities, satellite's ground station's transmissions and ground-based microwave communications.[68]
In popular culture[edit]
The television series Alias made recurring references to ECHELON throughout its run.
The antagonist of the anime series Digimon Tamers, D-Reaper, was created by ECHELON.
Echelon Conspiracy, inspired by the surveillance system ECHELON, is a 2009 action thriller film directed by Greg Marcks. It tells the story of Max Peterson (Shane West), an American computer specialist who attempts to uncover a secret plot to turn the world into a global police state. After being chased down by NSA agent Raymond Burke (Martin Sheen), Peterson decides to flee to Moscow.
The video game series Tom Clancy's Splinter Cell also draws inspiration from this. The series features the protagonist, Sam Fisher, a trained operative belonging to a fictional branch of the National Security Agency called Third Echelon (later, in Splinter Cell: Blacklist, the unit is replaced by the Fourth Echelon).
The 2007 film The Bourne Ultimatum makes several references to ECHELON. A CIA listening station in London is alerted when ECHELON detects the keyword "Blackbriar" in a cell phone conversation between a journalist and his editor.[69] Later in the film, CIA Deputy Director Pamela Landy requests an "ECHELON package" on the main character, Jason Bourne.
Alternative rock band Thirty Seconds to Mars' first album includes a song called "Echelon". Their fan base is also referred to as the Echelon, though an explanation has not been given as to why the fanbase and the song are referred to as such.
In the 2000 computer game Deus Ex, the signals intelligence supercomputers Daedalus and Icarus (later Helios) are referred to as Echelon IV.
The sci-fi crime thriller, Person of Interest, a television show which aired from 2011 to 2016 on the CBS network, had a data-collecting supercomputer as its central narrative.
See also[edit]
 Intelligence portal
Intelligence portal Mass surveillance portal
Mass surveillance portal2013 mass surveillance disclosures
ADVISE
Frenchelon
List of government surveillance projects
Mass surveillance
Onyx (interception system), the Swiss "Echelon"
Operation Ivy Bells
Carnivore (software)Carnivore, later renamed DCS1000, was a system implemented by the Federal Bureau of Investigation that was designed to monitor email and electronic communications. It used a customizable packet sniffer that can monitor all of a target user's Internet traffic. Carnivore was implemented in October 1997. By 2005 it had been replaced with improved commercial software.[1]
Contents [hide]
1Development
2Configuration
3Controversy
4Successor
5See also
6References
7External links
Development[edit]
Carnivore grew out of an earlier FBI project called "Omnivore", which itself replaced an older surveillance tool migrated from the US Navy by FBI Director of Integrity and Compliance,[2] Patrick W. Kelley, which had a still undisclosed name. In September 1998, the FBI's Data Intercept Technology Unit (DITU) in Quantico, Virginia, launched a project to migrate Omnivore from Sun's Solaris operating system to a Windows NT platform. This was done to facilitate the miniaturization of the system and support a wider range of personal computer (PC) equipment. The migration project was called "Phiple Troenix" and the resulting system was named "Carnivore."[3]
Configuration[edit]
The Carnivore system was a Microsoft Windows-based workstation with packet-sniffing software and a removable Jaz disk drive.[4] This computer must be physically installed at an Internet service provider (ISP) or other location where it can "sniff" traffic on a LAN segment to look for email messages in transit. The technology itself was not highly advanced—it used a standard packet sniffer and straightforward filtering. The critical components of the operation were the filtering criteria. To accurately match the appropriate subject, an elaborate content model was developed.[5] An independent technical review of Carnivore for the Justice Department was prepared in 2000.[6]
Controversy[edit]
Several groups expressed concern regarding the implementation, usage, and possible abuses of Carnivore. In July 2000, the Electronic Frontier Foundationsubmitted a statement to the Subcommittee on the Constitution of the Committee on the Judiciary in the United States House of Representatives detailing the dangers of such a system.[7] The Electronic Privacy Information Center also made several releases dealing with it.[8]
The FBI countered these concerns with statements highlighting the target-able nature of Carnivore. Assistant FBI Director Donald Kerr was quoted as saying:
The Carnivore device works much like commercial "sniffers" and other network diagnostic tools used by ISPs every day, except that it provides the FBI with a unique ability to distinguish between communications which may be lawfully intercepted and those which may not. For example, if a court order provides for the lawful interception of one type of communication (e.g., e-mail), but excludes all other communications (e.g., online shopping) the Carnivore tool can be configured to intercept only those e-mails being transmitted either to or from the named subject.
... [it] is a very specialized network analyzer or "sniffer" which runs as an application program on a normal personal computer under the Microsoft Windows operating system. It works by "sniffing" the proper portions of network packets and copying and storing only those packets which match a finely defined filter set programmed in conformity with the court order. This filter set can be extremely complex, and this provides the FBI with an ability to collect transmissions which comply with pen register court orders, trap & trace court orders, Title III interception orders, etc....
...It is important to distinguish now what is meant by "sniffing." The problem of discriminating between users' messages on the Internet is a complex one. However, this is exactly what Carnivore does. It does NOT search through the contents of every message and collect those that contain certain key words like "bomb" or "drugs." It selects messages based on criteria expressly set out in the court order, for example, messages transmitted to or from a particular account or to or from a particular user.[9]
After prolonged negative coverage in the press, the FBI changed the name of its system from "Carnivore" to the more benign-sounding "DCS1000." DCS is reported to stand for "Digital Collection System"; the system has the same functions as before.
Successor[edit]
The Associated Press reported in mid-January 2005 that the FBI essentially abandoned the use of Carnivore in 2001, in favor of commercially available software, such as NarusInsight, a mass surveillancesystem.[1] A report in 2007 described the successor system as being located "inside an Internet provider's network at the junction point of a router or network switch" and capable of indiscriminately storing data flowing through the provider's network.[10]
See also[edit]
 Government of the United States portal
Government of the United States portal Intelligence portal
Intelligence portal mass surveillance portal
mass surveillance portalCommunications Assistance For Law Enforcement Act
DITU
Harris corporation
Total Information Awareness
Surveillance
COINTELPRO
DCSNet
Echelon NSA worldwide digital interception program
Room 641A NSA interception program (started circa 2003, but first reported in 2006)
Policeware
Data Warehouse System Electronic Surveillance Data Management System
Magic Lantern (software)
Dishfire (stylised DISHFIRE) is a covert global surveillance collection system and database run by the United States of America's National Security Agency (NSA) and the United Kingdom's Government Communications Headquarters (GCHQ) that collects hundreds of millions of text messages on a daily basis from around the world.[1] A related analytic tool is known as Prefer
Contents
[hide]
1Details
2Scope of surveillance
3Data processing
4Reactions
5Gallery
6See also
7References
Details[edit]
The database is operated by the following agencies:
United States of America - National Security Agency (NSA)[2]
United Kingdom - Government Communications Headquarters (GCHQ) [2]
The existence of the database was revealed in 2014 based on documents disclosed by whistleblower Edward Snowden.[3] According to Snowden's documents, Britain's Government Communications Headquarters (GCHQ) has been given full access to the Dishfire database, which the agency uses to obtain personal information of Britons by exploiting a legal loophole
Stone Ghost STONEGHOST or "Stone Ghost", is a codename for a network operated by the United States' Defense Intelligence Agency (DIA) for information sharing and exchange between the United States, the United Kingdom, Canada and Australia.[1] Other sources say that New Zealand is also participating, and that Stone Ghost therefore connects, and is maintained by the defense intelligence agencies of all Five Eyes countries.[2]
Stone Ghost does not carry Intelink-Top Secret information. It used to be known as Intelink-C and may also be referred to as "Q-Lat" or "Quad link".[1] It is a highly secured network with strict physical and digital security requirements. The network hosts information about military topics, and about SIGINT, foreign intelligence and national security.[2]
2012 Canadian spy case[edit]
Royal Canadian Navy intelligence officer Sub-Lt. Jeffrey Delisle pleaded guilty on 10 October 2012 to charges including having downloaded and sold information from the Stone Ghost system to the Russian spy agency GRU.[3][4] He was sentenced to 20 years in prison, minus time served on February 6, 2013 for contravening the Security of Information Act.[5][6
Tempora empora is the codeword for a formerly secret computer system that is used by the British Government Communications Headquarters (GCHQ). This system is used to buffer most Internet communications that are extracted from fibre-optic cables, so these can be processed and searched at a later time.[2] It was tested since 2008 and became operational in the autumn of 2011.[3]
Tempora uses intercepts on the fibre-optic cables that make up the backbone of the Internet to gain access to large amounts of Internet users' personal data, without any individual suspicion or targeting. The intercepts are placed in the United Kingdom and overseas, with the knowledge of companies owning either the cables or landing stations.[4]
The existence of Tempora was revealed by Edward Snowden, a former American intelligence contractor who leaked information about the program to former Guardianjournalist Glenn Greenwald in May 2013, as part of his revelations of government-sponsored mass surveillance programs. Documents Snowden acquired claimed that data collected by the Tempora program is shared with the National Security Agency of the United States.[5]
Contents [hide]
1Operation
2Reactions
3See also
4References
5External links
Operation[edit]
According to Edward Snowden, Tempora has two principal components called "Mastering the Internet" (MTI) and "Global Telecoms Exploitation" (GTE). He claimed that each is intended to collate online and telephone traffic.[5] This however contradicts two original documents, which say that Tempora is only for Internet traffic, just like the XKeyscore system of the NSA, components of which are incorporated in Tempora.[2][6]
It is alleged that GCHQ produces larger amounts of metadata than NSA. By May 2012 300 GCHQ analysts and 250 NSA analysts had been assigned to sort data.[5]
The Guardian claims that no distinction is made in the gathering of data between public citizens and targeted suspects.[5] Tempora is said to include recordings of telephone calls, the content of email messages, Facebook entries and the personal Internet history of users. Snowden said of Tempora that "It's not just a U.S. problem. The UK has a huge dog in this fight...They [GCHQ] are worse than the U.S."[5]
Claims exist that Tempora was possible only by way of secret agreements with commercial companies, described in Snowden's leaked documents as "intercept partners". Some companies are alleged to have been paid for their co-operation. Snowden also alleged that GCHQ staff were urged to disguise the origin of material in their reports for fear that the role of the companies as intercept partners would cause "high-level political fallout".[5] The companies are forbidden to reveal the existence of warrants compelling them to allow GCHQ access to the cables. If the companies fail to comply they can be compelled to do so.[5]
Lawyers for GCHQ said it would be impossible to list the total number of people targeted by Tempora because "this would be an infinite list which we couldn't manage".[5]
GCHQ set up a three-year trial at the GCHQ Bude in Cornwall. GCHQ had probes attached to more than 201 Internet links by Summer 2011; each probe carried 10 gigabits of data a second.[5] NSA analysts were brought into the trials, and Tempora was launched in Autumn 2011, with data shared with the NSA. Ongoing technical work is expanding GCHQ's capacity to collect data from new super cables that carry data at 100 gigabits a second.[5] The data is preserved for three days while metadata is kept for thirty days.[1]
TEMPORA comprises different components, like the actual access points to fiber-optic cables, a sanitisation program codenamed POKERFACE, the XKEYSCOREsystem developed by NSA, and a Massive Volume Reduction (MVR) capability.[2]
In May 2012, GCHQ had TEMPORA systems installed at the following locations:[2]
16 for 10 gigabit/second cables at the CPC processing centre
7 for 10 gigabit/second cables at the OPC processing centre
23 for 10 gigabit/second cables at the RPC1 processing centre
Reactions[edit]
UK Defence officials issued a confidential DA-Notice to the BBC and other media asking the media to refrain from running further stories related to surveillance leaks including US PRISM program and the British involvement therein.[7][8]
The US Army has restricted its employees' access to the Guardian website since the beginning of the NSA leaks of PRISM and Tempora "in order to prevent an unauthorized disclosure of classified information."[9]
German Federal Minister of Justice Sabine Leutheusser-Schnarrenberger tweeted that she considered the program an "Alptraum" ("nightmare") and demanded that European institutions investigate the matter.[10][11]
Jan Philipp Albrecht, German Member of the European Parliament and spokesperson for Justice and Home Affairs of the Greens/EFA parliamentary group, called for an infringement procedure against the United Kingdom for having violated its obligations relating to the protection of individuals with regard to the processing of personal data under Article 16 of the Treaties of the European Union.[12]
Frenchelon is the nickname given to signal intelligence system used by France in reference to its Anglo-American counterpart ECHELON Its existence has never been officially acknowledged by French authorities, although numerous journalists, based on military information have mentioned it, since the European Parliament investigated ECHELON and also its implications in counter-terrorism. The term was coined by Kenneth Cukier, an American journalist living in Paris, in a paper presented at the Computers, Freedom and Privacy conference in 1999, and later in an op-ed in The Wall Street Journal Europe edition.[2]
Operations[edit]
The system is allegedly operated by DGSE, whose Direction Technique (Technical Direction) is responsible for signal intelligence. The largest station is in Domme, near Sarlat in Périgord. Some of the other stations in France are: Alluets-Feucherolles (Alluets-le-Roi), Mutzig (Alsace), Mont Valérien, Plateau d'Albion, Agde, Solenzara (South Corsica), and Filley Barracks in Nice.

A DGSE site near Saint-Christol
There are some other stations in overseas territories and former colonies:
Saint-Barthélemy
Bouar
Djibouti (Camp Lemonnier - closed, now occupied by Combined Joint Task Force – Horn of Africa) : new center built recently between French Air Force Base and French Foreign Legion camp in Djibouti.
Mayotte (Closed in 1998)
Réunion
Kourou
and base aeronavale La Tontouta in New Caledonia
These stations, in addition to the DGSE headquarters on boulevard Mortier in Paris, intercept electronic communications, decipher using software coded communications of diplomatic, military or industrial origin.
French newspapers recently indicated that DGSE had an interception program on submarine cables, similar to NSA ones. No official data indicates whether this could be a part of FRENCHELON.
It shouldn't be confused with the French Army's official listening system Emeraude,[3] which used to be mistakenly confused with Frenchelon
Fairview (surveillance program) Fairview is a secret program under which the National Security Agency cooperates with the American telecommunications company AT&T in order to collect phone, internet and e-mail data mainly of foreign countries' citizens at major cable landing stations and switching stations inside the United States. The FAIRVIEW program started in 1985, one year after the Bell breakup
The "key corporate partner" for cooperation under the FAIRVIEW program was first identified on October 23, 2013 by The Washington Post—quoting NSA historian Matthew Aid—as AT&T.[2]
This was confirmed by a joint report by Pro Publica and The New York Times from August 15, 2015, based upon NSA documents that describe the company as "highly collaborative" and praise the company’s "extreme willingness to help".[1]
In 2011, the FAIRVIEW program cost the NSA $188.9 million, which was twice as much as the costs for STORMBREW, which is the second-largest program.[1]
Scope of the program[edit]
According to 2013 revelations by whistleblower Edward Snowden:
The NSA partners with a large US telecommunications company...[which] partners with telecoms in the foreign countries, [which] then allow the US company access to those countries' telecommunications systems, and that access is then exploited to direct traffic to the NSA's repositories.[3]
According to the revelations, the NSA had collected 2.3 billion separate pieces of data from Brazilian users in January 2013 alone.[4]
Several weeks earlier, Snowden had revealed that the NSA was also harvesting the telephone metadata and text messages from over a billion subscribers in China; however, no precise program name was reported at the time.[5]

FAIRVIEW: Map shown on Brazilian television in 2013
A slide about the FAIRVIEW program that was seen on Brazilian television in 2013 showed a map with markers all over the United States, but without a legend that explained what they stood for. From a similar map with the proper legend, that was published in August 2015, it became clear that in 2010 the NSA had access to the following AT&T facilities:[6]
8 internet peering points
26 VoIP router facilities
1 VoIP hub router facility (with 30 planned)
9 submarine cable landing points (with 7 planned)
16 4ESS circuit switching stations
Except for the VoIP facilities, most of these access points are situated along the US borders.
MYSTIC (surveillance program) MYSTIC is a formerly secret program used since 2009 by the US National Security Agency (NSA) to collect the metadata as well as the content of phone calls from several entire countries. The program was first revealed in March 2014, based upon documents leaked by Edward Snowden.
MYSTIC operates under the legal authority of Executive Order 12333.
The MYSTIC program started in 2009, but reached its full extent, the capability to record the content of phone calls for an entire country for 30 days, in 2011. Documents from 2013 say the surveillance program could be extended to other countries.[1]
On March 18, 2014, the existence of the program was first revealed by The Washington Post, based upon documents leaked by Edward Snowden. It was reported that the NSA had the capability to record all the phone calls from an unidentified foreign country.[1]
On May 19, 2014, the website The Intercept published the name of one country of which the phone calls were recorded, and also identified three other countries of which only the telephony metadata were collected (see below).[2]
Scope[edit]
Under a sub-program of MYSTIC codenamed SOMALGET, the NSA is actively recording and archiving the content of "virtually every" phone call for thirty days. After thirty days, the recorded calls are overwritten by newer phone calls, although concern was raised that the NSA may start storing collected phone calls indefinitely.[3][4]
Although NSA analysts can only listen to less than 1% of the phone calls collected under MYSTIC, millions of voice clips are forwarded for processing and storage every month.[1]
A representative of the American Civil Liberties Union (ACLU) criticized the program, stating that the NSA now has the ability to record anything it wants to.[4] It was also noted that MYSTIC is the first revealed NSA surveillance operation capable of monitoring and recording an entire nation's telecommunication system.[5]
Targets[edit]
As of 2013, the NSA collected the metadata of phone calls from five entire countries, according to a report by The Intercept from May 19, 2014: Mexico, the Philippines, Kenya, the Bahamas and an initially unidentified country.[2]
For the latter two countries, the NSA not only collected the metadata, but also the content of phone calls. This took place under the SOMALGET sub-program.
The NSA documents purport that unlawful mass surveillance of the Bahamas resulted in the apprehension of narcotics traffickers.[6] The US government has also not yet shared information with the Bahamas, despite indicating that it would.[7]
Afghanistan[edit]
In March 2014, former NSA Deputy Director John C. Inglis had already said that the other country was Iraq,[8] but on May 19, an analysis published on the website Cryptome identified the country as Afghanistan.[9][10] Several days later, on May 23, WikiLeaks also reported that Afghanistan was the country of which the NSA collected nearly all phone calls.[11]
On September 9, 2015, US Director of National Intelligence James Clapper said that the disclosure of what reporters believed to be the MYSTIC and/or SOMALGET program, led the Afghan government to immediately close down an important intelligence program, that "was the single most important source of force protection and warning for our people in Afghanistan", according to Clapper
Digital Collection System Network The Digital Collection System Network (DCSNet) is the Federal Bureau of Investigation (FBI)'s point-and-click surveillance system that can perform instant wiretaps on almost any telecommunications device in the US.[1]
It allows access to cellphone, landline, SMS communications anywhere in the US from a point-and-click interface. It runs on a fiber-optic backbone separate from the internet.[2] It is intended to increase agent productivity through workflow modeling allowing for the routing of intercepts for translation or analysis with only a few clicks. DCSNet real-time intelligence data intercept has the capability to record, review and playback intercepted material in real-time.[1]
The DCSNET systems operates on a virtual private network parallel to the public internet, with services provided at least for some time by the Sprint peerless IP network.[3]
Much of the information available on this system has come from the results of Freedom of Information Act (FOIA) requests made by the Electronic Frontier Foundation(EFF).[4]
It is composed of at least three classified software components that run on the Windows operating system—DCS3000, DCS5000, DCS6000.
DCS-1000[edit]
Main article: Carnivore (software)
DCS-3000[edit]
DCS-3000 and "Red Hook" were first mentioned publicly in a March 2006 report from the United States Department of Justice Office of the Inspector General on the implementation of the Communications Assistance for Law Enforcement Act (CALEA).[5] The report described Red Hook as "a system to collect voice and data calls and then process and display the intercepted information in the absence of a CALEA solution."[5] and it described DCS-3000 "as an interim solution to intercept personal communications services delivered via emerging digital technologies used by wireless carriers in advance of any CALEA solutions being deployed."[5]
Citing the OIG report, the Electronic Frontier Foundation (EFF) filed an FOIA request later that year in order to obtain more information about the two programs. When the FBI did not respond with more information, the EFF sued, and in May 2007 obtained a court order to release documents concerning the programs.[6][7]
On August 29, 2007, Wired magazine published an article on these systems, citing the EFF documents.[1] The DCS-3000 collects information associated with dialed and incoming numbers like traditional trap-and-trace and pen registers. The article named "Red Hook" as the client for DCS-3000.[1]
DCS-5000[edit]
The DCS-5000 is a system used by the FBI unit responsible for counter-intelligence to target suspected spies, alleged terrorists, and others with wiretaps.
DCS-6000[edit]
The DCS-6000 captures the content of phone calls and text messages for analysis
Boundless Informant Boundless Informant (stylized as BOUNDLESSINFORMANT) is a big data analysis and data visualization tool used by the United States National Security Agency (NSA). It gives NSA managers summaries of the NSA's worldwide data collection activities by counting metadata.[1] The existence of this tool was disclosed by documents leaked by Edward Snowden, who worked at the NSA for the defense contractor Booz Allen Hamilton.[2] Those disclosed documents were in a direct contradiction to the NSA's assurance to United States Congress that it does not collect any type of data on millions of Americans
Intelligence gathered by the United States government inside the United States or specifically targeting US citizens is legally required to be gathered in compliance with the Foreign Intelligence Surveillance Act of 1978 (FISA) and under the authority of the Foreign Intelligence Surveillance Court (FISA court).[4][5][6]
NSA global data mining projects have existed for decades, but recent programs of intelligence gathering and analysis that include data gathered from inside the United States such as PRISM were enabled by changes to US surveillance law introduced under President Bush and renewed under President Obama in December 2012.[7]
Boundless Informant was first publicly revealed on June 8, 2013, after classified documents about the program were leaked to The Guardian.[1][8] This report contained a Top Secret heat map produced by the Boundless Informant program summarizing data records from 504 separate DNR and DNI collection sources or SIGADs. In the map, countries that are under surveillance are assigned a color from green to red (which does not correspond to intensity of surveillance).[9][10]

The worldwide heat map from the NSA's data visualisation tool BOUNDLESSINFORMANT, showing that during a 30-day period, 97 billion internet data records (DNI) and 124 billion telephony data records (DNR) were collected.
As this map shows that almost 3 billion data elements from inside the United States were captured by the NSA over a 30-day period ending in March 2013, Snowden stated that this tool was collecting more information on Americans located within the United States than on Russians in Russia.[11] Snowden stated that he raised concerns with two superiors in the Hawaii regional base of the NSA Threat Operations Center and two superiors in the Technology Directorate of the NSA beginning in October 2012, and therefore that counted as using internal dissent channels in the NSA.[11]
Snowden added that coworkers often were "astonished to learn" about this detail and did not wish to know any more about the program, and that until April 2012 he often asked these colleagues "What do you think the public would do if this was on the front page?"[11] Vanee Vines, an NSA spokesperson, stated that "After extensive investigation, including interviews with his former NSA supervisors and co-workers, we have not found any evidence to support Mr. Snowden’s contention that he brought these matters to anyone’s attention."[11]
The first publication about Boundless Informant was followed by screenshots from this program showing charts with details about the data that NSA allegedly collected from several European countries between December 10, 2012 and January 8, 2013. These charts were published by a major news outlet from each of these countries:

Screenshot from the BOUNDLESSINFORMANT tool, showing charts with different details about data collection related to Germany. The upper chart shows internet (blue bars) and telephony (green bars) data, the bottom center chart mentions two SIGADs and the most important "tech" in the bottom right section is the XKeyscore program.
July 29, 2013: Germany: a big chart about this country, showing more than 552 million telephony and internet data, alongside four smaller charts about The Netherlands, France, Spain and Italy were published by the magazine Der Spiegel.[12]
October 20, 2013: France: a chart showing almost 70 million telephony metadata was published by the newspaper Le Monde.
October 28, 2013: Spain: a chart showing 60 million telephony metadata was published by the newspaper El Mundo.[13]
November 19, 2013: Norway: a chart showing 33 million telephony metadata was published by the tabloid paper Dagbladet.[14]
December 6, 2013: Italy: a chart showing almost 46 million telephony metadata was published by the tabloid paper L'Espresso.[15]
February 8, 2014: The Netherlands: a chart showing 1,8 million telephony metadata was published by the newspaper NRC Handelsblad.[16]
Initially, these media wrote that the BoundlessInformant charts showed how much phonecalls NSA intercepted from a particular country. A first correction of this interpretation is that the program doesn't count the content of phone calls, but only the metadata thereof (see below).
A second correction is about by whom and where these data were collected. On August 5, a week after the publication of a chart from BoundlessInformant in Germany, the German intelligence agency BND said that they collected these data from foreign communications, related to military operations abroad.[17][18] A similar statement was made by the Norwegian military intelligence service, after a chart about Norway was published on November 19.[19] On February 4, 2014, the Dutch government revealed that the 1,8 million metadata in the chart about the Netherlands were not collected by NSA, but instead by the Dutch military intelligence service MIVD, also to support military operations, which almost led to the resignation of the Dutch interior minister.[20]
On October 29, 2013, NSA-director Keith B. Alexander declared that accusations in French, Spanish and Italian media about NSA intercepting millions of phone calls from these countries are "completely false". He added that "This is not information that we collected on European citizens. It represents information that we and our NATO allies have collected in defense of our countries and in support of military operations."[21]
Technology[edit]
Although the initial reports in European media stated that the various charts presented the numbers of phone calls intercepted by NSA, a powerpoint presentation and a FAQ document published by The Guardian[22] say that BoundlessInformant is counting and analysing DNI (internet) and DNR (telephony) metadata records passing through the NSA's signals intelligence systems, and are therefore not showing how much content of internet and telephone communications is intercepted.[23]
Data analyzed by Boundless Informant includes electronic surveillance program records and telephone call metadata records stored in an NSA data archive called GM-PLACE. It does not include FISA data, according to the FAQ memo. PRISM, a government codename for a collection effort known officially as US-984XN, which was revealed at the same time as Boundless Informant, is one source of DNR data.[9][10]
According to published slides, Boundless Informant leverages Free and Open Source Software—and is therefore "available to all NSA developers"—and corporate services hosted in the cloud. The tool uses HDFS, MapReduce, and Accumulo (formerly Cloudbase)[24] for data processing.[25]]
Bullrun (decryption program)

National Security Agencysurveillance

Map of global NSA data collection
Programs[show]
Legislation[show]
Institutions[show]
Lawsuits[show]
Whistleblowers[show]
Publication[show]
Related[show]
Concepts[show]
Collaboration[show]
v
t
e

Bullrun classification guide published by theguardian.com
Bullrun (stylized BULLRUN) is a clandestine, highly classified program to crack encryption of online communications and data, which is run by the United States National Security Agency (NSA).[1][2] The British Government Communications Headquarters (GCHQ) has a similar program codenamed Edgehill. According to the BULLRUN classification guide published by The Guardian, the program uses multiple methods including computer network exploitation,[3] interdiction, industry relationships, collaboration with other intelligence community entities, and advanced mathematical techniques.
Information about the program's existence was leaked in 2013 by Edward Snowden. Although Snowden's documents do not contain technical information on exact cryptanalytic capabilities because Snowden did not have clearance access to such information,[4] they do contain a 2010 GCHQ presentation which claims that "vast amounts of encrypted Internet data which have up till now been discarded are now exploitable".[1] A number of technical details regarding the program found in Snowden's documents were additionally censored by the press at the behest of US intelligence officials.[5] Out of all the programs that have been leaked by Snowden, the Bullrun Decryption Program is by far the most expensive. Snowden claims that since 2011, expenses devoted to Bullrun amount to $800 million. The leaked documents reveal that Bullrun seeks to "defeat the encryption used in specific network communication technologies"
Naming and access[edit]
According to the NSA's BULLRUN Classification Guide, BULLRUN is not a Sensitive Compartmented Information (SCI) control system or compartment, but the codeword has to be shown in the classification line, after all other classification and dissemination markings. Furthermore, any details about specific cryptographic successes were recommend to be additionally restricted (besides being marked Top Secret//SI) with Exceptionally Controlled Information labels; a non-exclusive list of possible BULLRUN ECI labels was given as: APERIODIC, AMBULANT, AUNTIE, PAINTEDEAGLE, PAWLEYS, PITCHFORD, PENDLETON, PICARESQUE, and PIEDMONT without any details as to what these labels mean.[1][2]
Access to the program is limited to a group of top personnel at the Five Eyes (FVEY), the NSA and the signals intelligence agencies of the United Kingdom (GCHQ), Canada (CSE), Australia (ASD), and New Zealand (GCSB). Signals that cannot be decrypted with current technology may be retained indefinitely while the agencies continue to attempt to decrypt them.[2]
Methods[edit]

Slide published by the Guardian diagramming the high-level architecture of NSA's "Exploitation [Cracking] of Common Internet Encryption Technologies"
Through the NSA-designed Clipper chip which used the Skipjack cipher with an intentional backdoor, and using various specifically designed laws such as CALEA, CESA and restrictions on export of encryption software as evidenced by Bernstein v. United States, the U.S. government had publicly attempted in the 1990s to ensure its access to communications and ability to decrypt.[7][8] In particular, technical measures such as key escrow, a euphemism for a backdoor, have met with criticism and little success.
The NSA encourages the manufacturers of security technology to disclose backdoors to their products or encryption keys so that they may access the encrypted data.[9] However, fearing widespread adoption of encryption, the NSA set out to stealthily influence and weaken encryption standards and obtain master keys—either by agreement, by force of law, or by computer network exploitation (hacking).[5]
According to a Bullrun briefing document, the agency had successfully infiltrated both the Secure Sockets Layer as well as virtual private network (VPN).[1][2] The New York Times reported that: "But by 2006, an N.S.A. document notes, the agency had broken into communications for three foreign airlines, one travel reservation system, one foreign government's nuclear department and another's Internet service by cracking the virtual private networks that protected them. By 2010, the Edgehill program, the British counterencryption effort, was unscrambling VPN traffic for 30 targets and had set a goal of an additional 300."[5]
As part of Bullrun, NSA has also been actively working to "Insert vulnerabilities into commercial encryption systems, IT systems, networks, and endpoint communications devices used by targets".[10] The New York Times has reported that the random number generator Dual_EC_DRBG contains a back door, which would allow the NSA to break encryption keys generated by the random number generator.[11] Even though this random number generator was known to be insecure and slow soon after the standard was published, and a potential NSA kleptographic backdoor was found in 2007 while alternative random number generators without these flaws were certified and widely available, RSA Security continued using Dual_EC_DRBG in the company's BSAFE toolkit and Data Protection Manager until September 2013. While RSA Security has denied knowingly inserting a backdoor into BSAFE, it has not yet given an explanation for the continued usage of Dual_EC_DRBG after its flaws became apparent in 2006 and 2007.[12] It was reported on December 20, 2013 that RSA had accepted a payment of $10 million from the NSA to set the random number generator as the default.[13][14] Leaked NSA documents state that their effort was “a challenge in finesse” and that “Eventually, N.S.A. became the sole editor” of the standard.[5]
By 2010, the leaked documents state that the NSA had developed "groundbreaking capabilities" against encrypted Internet traffic. A GCHQ document warned however "These capabilities are among the SIGINT community's most fragile, and the inadvertent disclosure of the simple 'fact of' could alert the adversary and result in immediate loss of the capability."[5] Another internal document stated that "there will be NO 'need to know.'"[5] Several experts, including Bruce Schneier and Christopher Soghoian, have speculated that a successful attack against RC4, an encryption algorithm still used in at least 50 percent of all SSL/TLS traffic, is a plausible avenue, given several publicly known weaknesses of RC4.[15] Others have speculated that NSA has gained ability to crack 1024-bit RSA/DH keys.[16]
Fallout[edit]
In the wake of BULLRUN revelations, some open source projects, including FreeBSD and OpenSSL, have seen an increase in their reluctance to (fully) trust hardware-based cryptographic primitives.[17][18]
Many other software projects, companies and organizations responded with an increase in the evaluation of their security and encryption processes. For example, Google doubled the size of their TLS-certificates from 1024 bits to 2048 bits.[19]
Revelations of the NSA backdoors and purposeful complication of standards has led to a backlash in their participation in standards bodies.[20] Prior to the revelations the NSA's presence on these committees was seen as a benefit given their expertise with encryption.[21]
There has been speculation that the NSA was aware of the Heartbleed bug, which caused major websites to be vulnerable to password theft, but did not reveal this information in order to exploit it themselves.[22]
Pinwale Pinwale is the code name for an NSA collection and retrieval system for so-called "Digital Network Intelligence", including internet e-mail.[1][2] It is searchable by monitored NSA analysts.
The existence of the system was first revealed by an NSA analyst who was trained in its use during 2005.[2] However, according to Homeland Security Today, Pinwale has in it much more than email, it also contains other forms of Internet data, and other forms of digital communications as well. Its software has built-in protections against collecting from any of the Five Eyes members. Unlike its successor XKeyscore, targets for PINWALE have to be approved beforehand by the FISC.[1]
According to information obtained by The Guardian from Edward Snowden, Pinwale is part of a "multi-tiered system" to address the issue of NSA "collecting so much internet data that it can be stored only for short periods of time." The system allows analysts to store "interesting" content in databases such as Pinwale, which is capable of storing material for up to five years.[3]
Pinwale consists of at least two known partitions referred to as "Sweet" and "Sour".[4]
According to the documents leaked by Snowden, Pinwale normally processed about 60 GB of data per day without trouble. Pinwale was overwhelmed however when Yahoo started mass mailbox transfers between its datacenters, which were captured by the NSA's MUSCULAR program that taps the private clouds of Google and Yahoo. Monitored email accounts being hacked by spammers also present a challenge to Pinwale, because they can cause the database of suspect email addresses to grow exponentially with information of no intelligence value.[5]
Stingray phone tracker

A Stingray device in 2013, in Harris's trademark submission.[1]
The StingRay is an IMSI-catcher, a controversial cellular phone surveillance device, manufactured by Harris Corporation.[2] Initially developed for the military and intelligence community, the StingRay and similar Harris devices are in widespread use by local and state law enforcement agencies across Canada,[3] the United States,[4][5] and in the United Kingdom.[6][7] Stingray has also become a generic name to describe these kinds of devices.[8

When operating in active mode, the Stingray device mimics a wireless carrier cell tower in order to force all nearby mobile phones and other cellular data devices to connect to it.
The StingRay is an IMSI-catcher with both passive (digital analyzer) and active (cell-site simulator) capabilities. When operating in active mode, the device mimics a wireless carrier cell tower in order to force all nearby mobile phones and other cellular data devices to connect to it.[9][10][11]
The StingRay family of devices can be mounted in vehicles,[10] on aeroplanes, helicopters and unmanned aerial vehicles.[12] Hand-carried versions are referred to under the trade name KingFish.[13]
Active mode operations[edit]
Extracting stored data such as International Mobile Subscriber Identity ("IMSI") numbers and Electronic Serial Number ("ESN"),[14]
Writing cellular protocol metadata to internal storage
Forcing an increase in signal transmission power,[15]
Forcing an abundance of radio signals to be transmitted
Interception of communications content
Tracking and locating the cellular device user,[9]
Conducting a denial of service attack
Encryption key extraction.[16]
Radio jamming for either general denial of service purposes[17][not in citation given (See discussion.)] or to aid in active mode protocol rollback attacks
Passive mode operations[edit]
conducting base station surveys, which is the process of using over-the-air signals to identify legitimate cell sites and precisely map their coverage areas
Active (cell site simulator) capabilities[edit]
In active mode, the StingRay will force each compatible cellular device in a given area to disconnect from its service provider cell site (e.g., operated by Verizon, AT&T, etc.) and establish a new connection with the StingRay.[18] In most cases, this is accomplished by having the StingRay broadcast a pilot signal that is either stronger than, or made to appear stronger than, the pilot signals being broadcast by legitimate cell sites operating in the area.[19] A common function of all cellular communications protocols is to have the cellular device connect to the cell site offering the strongest signal. StingRays exploit this function as a means to force temporary connections with cellular devices within a limited area.
Extracting data from internal storage[edit]
During the process of forcing connections from all compatible cellular devices in a given area, the StingRay operator needs to determine which device is the desired surveillance target. This is accomplished by downloading the IMSI, ESN, or other identifying data from each of the devices connected to the StingRay.[14] In this context, the IMSI or equivalent identifier is not obtained from the cellular service provider or from any other third-party. The StingRay downloads this data directly from the device using radio waves.[20]
In some cases, the IMSI or equivalent identifier of a target device is known to the StingRay operator beforehand. When this is the case, the operator will download the IMSI or equivalent identifier from each device as it connects to the StingRay.[21] When the downloaded IMSI matches the known IMSI of the desired target, the dragnet will end and the operator will proceed to conduct specific surveillance operations on just the target device.[22]
In other cases, the IMSI or equivalent identifier of a target is not known to the StingRay operator and the goal of the surveillance operation is to identify one or more cellular devices being used in a known area.[23] For example, if visual surveillance is being conducted on a group of protestors,[24] a StingRay can be used to download the IMSI or equivalent identifier from each phone within the protest area. After identifying the phones, locating and tracking operations can be conducted, and service providers can be forced to turn over account information identifying the phone users.
Forcing an increase in signal transmission power
Cellular telephones are radio transmitters and receivers much like a walkie-talkie. However, the cell phone communicates only with a repeater inside a nearby cell tower installation. At that installation, the devices take in all cell calls in its geographic area and repeat them out to other cell installations which repeat the signals onward to their destination telephone (either by radio or landline wires). Radio is used also to transmit a caller's voice/data back to the receiver's cell telephone. The two-way duplex phone conversation then exists via these interconnections.
To make all that work correctly, the system allows automatic increases and decreases in transmitter power (for the individual cell phone and for the tower repeater, too) so that only the minimum transmit power is used to complete and hold the call active, "on," and allows the users to hear and be heard continuously during the conversation. The goal is to hold the call active but use the least amount of transmitting power, mainly to conserve batteries and be efficient. The tower system will sense when a cell phone is not coming in clearly and will order the cell phone to boost transmit power. The user has no control over this boosting; it may occur for a split second or for the whole conversation. If the user is in a remote location, the power boost may be continuous. In addition to carrying voice or data, the cell phone also transmits data about itself automatically, and that is boosted or not as the system detects need.
Encoding of all transmissions ensures that no cross talk or interference occurs between two nearby cell users. The boosting of power, however, is limited by the design of the devices to a maximum setting. The standard systems are not "high power" and thus can be overpowered by secret systems using much more boosted power that can then take over a user's cell phone. If overpowered that way, a cell phone will not indicate the change due to the secret radio being programmed to hide from normal detection. The ordinary user can not know if their cell phone is captured via overpowering boosts or not. (There are other ways of secret capture that need not overpower, too.)
Just as a person shouting drowns out someone whispering, the boost in RF watts of power into the cell telephone system can overtake and control that system—in total or only a few, or even only one, conversation. This strategy requires only more RF power, and thus it is more simple than other types of secret control. Power boosting equipment can be installed anywhere there can be an antenna, including in a vehicle, perhaps even in a vehicle on the move. Once a secretly boosted system takes control, any manipulation is possible from simple recording of the voice or data to total blocking of all cell phones in the geographic area.
Tracking and locating[edit]
A StingRay can be used to identify and track a phone or other compatible cellular data device even while the device is not engaged in a call or accessing data services.[citation needed]
A Stingray closely resembles a portable cellphone tower. Typically, law enforcement officials place the Stingray in their vehicle with a compatible computer software. The Stingray acts as a cellular tower to send out signals to get the specific device to connect to it. Cell phones are programmed to connect with the cellular tower offering the best signal. [116] When the phone and Stingray connect, the computer system determines the strength of the signal and thus the distance to the device. Then, the vehicle moves to another location and sends out signals until it connects with the phone. When the signal strength is determined from enough locations, the computer system centralizes the phone and is able to find it. [58]
Cell phones are programmed to constantly search for the strongest signal emitted from cell phone towers in the area. Over the course of the day, most cell phones connect and reconnect to multiple towers in an attempt to connect to the strongest, fastest, or closest signal. Because of the way they are designed, the signals that the Stingray emits are far stronger than those coming from surrounding towers. For this reason, all cell phones in the vicinity connect to the Stingray regardless of the cell phone owner’s knowledge. From there, the stingray is capable of locating the device, interfering with the device, and collecting personal data from the device [59].[25][26]
Denial of service[edit]
The FBI has claimed that when used to identify, locate, or track a cellular device, the StingRay does not collect communications content or forward it to the service provider.[27] Instead, the device causes a disruption in service.[28] Under this scenario, any attempt by the cellular device user to place a call or access data services will fail while the StingRay is conducting its surveillance.
Interception of communications content[edit]
By way of software upgrades,[16][29] the StingRay and similar Harris products can be used to intercept GSM communications content transmitted over-the-air between a target cellular device and a legitimate service provider cell site. The StingRay does this by way of the following man-in-the-middle attack: (1) simulate a cell site and force a connection from the target device, (2) download the target device's IMSI and other identifying information, (3) conduct "GSM Active Key Extraction"[16] to obtain the target device's stored encryption key, (4) use the downloaded identifying information to simulate the target device over-the-air, (5) while simulating the target device, establish a connection with a legitimate cell site authorized to provide service to the target device, (6) use the encryption key to authenticate the StingRay to the service provider as being the target device, and (7) forward signals between the target device and the legitimate cell site while decrypting and recording communications content.
The "GSM Active Key Extraction"[16] performed by the StingRay in step three merits additional explanation. A GSM phone encrypts all communications content using an encryption key stored on its SIM card with a copy stored at the service provider.[30] While simulating the target device during the above explained man-in-the-middle attack, the service provider cell site will ask the StingRay (which it believes to be the target device) to initiate encryption using the key stored on the target device.[31] Therefore, the StingRay needs a method to obtain the target device's stored encryption key else the man-in-the-middle attack will fail.
GSM primarily encrypts communications content using the A5/1 call encryption cypher. In 2008 it was reported that a GSM phone's encryption key can be obtained using $1,000 worth of computer hardware and 30 minutes of cryptanalysis performed on signals encrypted using A5/1.[32] However, GSM also supports an export weakened variant of A5/1 called A5/2. This weaker encryption cypher can be cracked in real-time.[30] While A5/1 and A5/2 use different cypher strengths, they each use the same underlying encryption key stored on the SIM card.[31] Therefore, the StingRay performs "GSM Active Key Extraction"[16] during step three of the man-in-the-middle attack as follows: (1) instruct target device to use the weaker A5/2 encryption cypher, (2) collect A5/2 encrypted signals from target device, and (3) perform cryptanalysis of the A5/2 signals to quickly recover the underlying stored encryption key.[33] Once the encryption key is obtained, the StingRay uses it to comply with the encryption request made to it by the service provider during the man-in-the-middle attack.[33]
Passive capabilities[edit]
In passive mode, the StingRay operates either as a digital analyzer, which receives and analyzes signals being transmitted by cellular devices and/or wireless carrier cell sites or as a radio jamming device, which transmits signals that block communications between cellular devices and wireless carrier cell sites. By "passive mode," it is meant that the StingRay does not mimic a wireless carrier cell site or communicate directly with cellular devices.
Base station (cell site) surveys[edit]
A StingRay and a test phone can be used to conduct base station surveys, which is the process of collecting information on cell sites, including identification numbers, signal strength, and signal coverage areas. When conducting base station surveys, the StingRay mimics a cell phone while passively collecting signals being transmitted by cell-sites in the area of the StingRay.
Base station survey data can be used to further narrow the past locations of a cellular device if used in conjunction with historical cell site location information ("HCSLI") obtained from a wireless carrier. HCSLI includes a list of all cell sites and sectors accessed by a cellular device, and the date and time each access was made. Law enforcement will often obtain HCSLI from wireless carriers in order to determine where a particular cell phone was located in the past. Once this information is obtained, law enforcement will use a map of cell site locations to determine the past geographical locations of the cellular device.
However, the signal coverage area of a given cell site may change according to the time of day, weather, and physical obstructions in relation to where a cellular device attempts to access service. The maps of cell site coverage areas used by law enforcement may also lack precision as a general matter. For these reasons, it is beneficial to use a StingRay and a test phone to map out the precise coverage areas of all cell sites appearing in the HCSLI records. This is typically done at the same time of day and under the same weather conditions that were in effect when the HCSLI was logged. Using a StingRay to conduct base station surveys in this manner allows for mapping out cell site coverage areas that more accurately match the coverage areas that were in effect when the cellular device was used.
Usage by law enforcement[edit]
In the United States[edit]
Main article: Stingray use in United States law enforcement
The use of the devices has been frequently funded by grants from the Department of Homeland Security.[34] The Los Angeles Police Department used a Department of Homeland Security grant in 2006 to buy a StingRay for "regional terrorism investigations".[35] However, according to the Electronic Frontier Foundation, the "LAPD has been using it for just about any investigation imaginable."[36]
In addition to federal law enforcement, military and intelligence agencies, StingRays have in recent years been purchased by local and state law enforcement agencies.
In 2006, Harris employees directly conducted wireless surveillance using StingRay units on behalf the Palm Bay Police Department — where Harris has a campus[37] — in response to a bomb threat against a middle school. The search was conducted without a warrant or Judicial oversight.[38][39][40][41]
The American Civil Liberties Union, commonly referred to as the ACLU, confirmed that local police have cell site simulators in Washington, Nevada, Arizona, Alaska, Missouri, Georgia, and Massachusetts. State police have cell site simulators in Oklahoma, Louisiana, and Pennsylvania, and Delaware. Local and state police have cell site simulators in California, Texas, Minnesota, Wisconsin, Michigan, Illinois, Indiana, Tennessee, North Carolina, Virginia, Florida, Maryland, and New York [60]. The police use of cell site simulators is unknown in the remaining states. However, many agencies do not disclose their use of StingRay technology, so these statistics are still potentially an under-representation of the actual number of agencies. According to the most recent information published by the American Civil Liberties Union, 72 law enforcement agencies in 24 states own StingRay technology in 2017. Since 2014, these numbers have increased from 42 agencies in 17 states [60]. The following are federal agencies in the United States that have validated their use of cell site simulators: Federal Bureau of Investigation, Drug Enforcement Administration, US Secret Service, Immigration and Customs Enforcement, US Marshals Service, Bureau of Alcohol, Tobacco, Firearms, and Explosives, US Army, US Navy, US Marine Corps, US National Guard, US Special Command, and National Security Agency [60].[42]
Several court decisions have been issued on the legality of using a Stingray without a warrant, with some courts ruling a warrant is required[43][44][45] and others not requiring a warrant.[46]
Outside the United States[edit]
Police in Vancouver, BC, Canada admitted after much speculation across the country that they had made use of a Stingray device[47] provided by the RCMP. They also stated that they intended to make use of such devices in the future. Two days later, a statement by Edmonton's police force had been taken as confirming their use of the devices, but they said later that they did not mean to create what they called a miscommunication.[48]
Privacy International and The Sunday Times reported on the usage of StingRays and IMSI-catchers in Ireland, against the Irish Garda Síochána Ombudsman Commission (GSOC), which is an oversight agency of the Irish police force Garda Síochána.[49][50] On June 10, 2015 the BBC reported on an investigation by Sky News[51][52] about possible false mobile phone towers being used by the London Metropolitan Police. Commissioner Bernard Hogan-Howe refused comment.
Between February 2015 and April 2016, over 12 companies in the United Kingdom were authorized to export IMSI-catcher devices to states including Saudi Arabia, UAE, and Turkey. Critics have expressed concern about the export of surveillance technology to countries with poor human rights records and histories of abusing surveillance technology.[53]
Secrecy[edit]
The increasing use of the devices has largely been kept secret from the court system and the public.[54] In 2014, police in Florida revealed they had used such devices at least 200 additional times since 2010 without disclosing it to the courts or obtaining a warrant.[2] One of the reasons the Tallahassee police provided for not pursuing court approval is that such efforts would allegedly violate the non-disclosure agreements (NDAs) that police sign with the manufacturer.[55] The American Civil Liberties Union has filed multiple requests for the public records of Florida law enforcement agencies about their use of the cell phone tracking devices.[56]
Local law enforcement and the federal government have resisted judicial requests for information about the use of stingrays, refusing to turn over information or heavily censoring it.[57] In June 2014, the American Civil Liberties Union published information from court regarding the extensive use of these devices by local Florida police.[58] After this publication, United States Marshals Service then seized the local police's surveillance records in a bid to keep them from coming out in court.[59]
In some cases, police have refused to disclose information to the courts citing non-disclosure agreements signed with Harris Corporation.[57][60][61] The FBI defended these agreements, saying that information about the technology could allow adversaries to circumvent it.[60] The ACLU has said "potentially unconstitutional government surveillance on this scale should not remain hidden from the public just because a private corporation desires secrecy. And it certainly should not be concealed from judges."[2]
In 2015 Santa Clara County pulled out of contract negotiations with Harris for StingRay units, citing onerous restrictions imposed by Harris on what could be released under public records requests as the reason for exiting negotiations.[62]
Criticism[edit]
In recent years, legal scholars, public interest advocates, legislators and several members of the judiciary have strongly criticized the use of this technology by law enforcement agencies. Critics have called the use of the devices by government agencies warrantless cell phone tracking, as they have frequently been used without informing the court system or obtaining a warrant.[2] The Electronic Frontier Foundationhas called the devices “an unconstitutional, all-you-can-eat data buffet.”[63]
In June 2015, WNYC Public Radio published a podcast with Daniel Rigmaiden about the StingRay device.[64]
In 2016, Professor Laura Moy of the Georgetown University Law Center filed a formal complaint to the FCC regarding the use of the devices by law enforcement agencies, taking the position that because the devices mimic the properties of cell phone towers, the agencies operating them are in violation of FCC regulation, as they lack the appropriate spectrum licenses.[65]
A number of countermeasures to the StingRay and other devices have been developed, for example crypto phones such as GMSK's Cryptophone have firewalls that can identify and thwart the StingRay's actions or alert the user to IMEI capture.[66] This can also be done with certain applications.
SORM SORM (Russian: Система оперативно-разыскных мероприятий, lit. 'System for Operative Investigative Activities') is the technical specification for lawful interception interfaces of telecommunications and telephone networks operating in Russia. The current form of the specification enables the targeted surveillance of both telephone and Internet communications. Initially implemented in 1995 to allow access to surveillance data for the FSB, in subsequent years the access has been widened to other law enforcement agencies.
SORM-1[edit]
SORM was first implemented in 1995, requiring telecommunications operators to install FSB-provided hardware allowing the agency to monitor users’ communications metadata and content. This included phone calls, email traffic and web browsing activity, despite the low internet penetration rate at the time.[1]
SORM-2[edit]
In July 1998 the system was replaced by SORM‑2. Under SORM‑2, Russian Internet service providers (ISPs) must install a special device on their servers to allow the FSB to track all credit card transactions,[citation needed] e-mail messages and web use.[2] The device must be installed at the ISP's expense.[3] It has been estimated to cost $10,000–$30,000.[citation needed] Other reports note that some ISPs have had to install direct communications lines to the FSB and that costs for implementing the required changes were in excess of $100,000.[citation needed]
In July 2000, Russia's Minister of Information Technology and Communications Leonid Reiman issued the order No 130 "Concerning the introduction of technical means ensuring investigative activity (SORM) in phone, mobile and wireless communication and radio paging networks" stating that the FSB was no longer required to provide telecommunications and Internet companies documentation on targets of interest prior to accessing information.[4]
In August 2014, SORM-2 usage was extended to monitoring of social networks, chats and forums, requiring their operators to install SORM probes in their networks.[5][6]
SORM-3[edit]
A ministerial order from the Russian Ministry of Communications from 16 April 2014 introduced requirements for the new wiretapping system SORM-3. Telecommunications operators were required to install compliant equipment by 31 March 2015.[7]
According to regulations of Russian Ministry of Communications[8] SORM-3 equipment supports the following selectors for targeted surveillance:
Single IPv4 or IPv6 address
IPv4 or IPv6 networks identified with address mask
User ID within telecom operator's system, supporting "*" and "?" as globbing symbols (wildcards)
e-mail address, if targeted user connects via POP3, SMTP or IMAP4; connections protected with cryptography are specifically excluded
e-mail address, if targeted user connects to a webmail system from a predefined list of services: mail.ru; yandex.ru; rambler.ru; gmail.com; yahoo.com; apport.ru; rupochta.ru; hotbox.ru; again, connections protected with cryptography are specifically excluded
User's phone number
IMSI
IMEI
MAC address of user's equipment
ICQ UIN
The equipment has deep packet inspection (DPI) capability.[1]
Architecture and deployment[edit]
Russia uses deep packet inspection (DPI) on a nationwide scale, with part of the DPI infrastructure used for SORM.[9] Some mobile networks use DPI to additionally filter traffic.[10]
The SORM device recommended by the FSB is named Omega.[10] Equipment by Cellebrite appears to be in use.[11] SORM also enables the use of mobile control points, a laptop that can be plugged directly into communication hubs and immediately intercept and record the operator's traffic.[3]
Roskomnadzor, a federal executive body responsible for media control, reported that several local ISPs were fined by the government after they failed to install FSB-recommended SORM devices.[10]
Access by government agencies[edit]
On January 5, 2000, during his first week in office, President Vladimir Putin amended the law to allow seven other federal security agencies (next to the FSB) access to data gathered via SORM. The newly endowed agencies included:[12][13]
Russia's tax police
Russian Police
Federal Protective Service
Border patrol and customs
Ministry of Internal Affairs
Kremlin Regiment
Presidential Security Service
Parliamentary security services
Warrant and notification regulations[edit]
The acquisition of communications by entitled security services in general requires a court warrant, but at the same time they are allowed to start wiretapping before obtaining such warrant. The warrant is also only required for communications content, but not metadata (communicating parties, time, location etc.), which may be obtained without the warrant.[14]
In cases where an FSB operative is required to get an eavesdropping warrant, he is under no obligation to show it to anyone. Telecom providers have no right to demand that the FSB provide a warrant, and are denied access to the surveillance boxes. The security service calls on the special controller at the FSB headquarters that is connected by a protected cable directly to the SORM device installed on the ISP network.[3]
Since 2010, intelligence officers can wiretap someone's phones or monitor their Internet activity based on received reports that an individual is preparing to commit a crime. They do not have to back up those allegations with formal criminal charges against the suspect.[15] According to a 2011 ruling, intelligence officers have the right to conduct surveillance of anyone who they claim is preparing to call for "extremist activity."[15]
Zakharov v. Russia[edit]
Main article: Zakharov v. Russia
In December 2015, The European Court of Human Rights ruled on a case on the legality of Russian SORM legislation.[16][17] In a unanimous Grand Chamber decision, the Court ruled that Russian legal provisions "do not provide for adequate and effective guarantees against arbitrariness and the risk of abuse which is inherent in any system of secret surveillance." It noted that this risk "is particularly high in a system where the secret services and the police have direct access, by technical means, to all mobile telephone communications." It ruled that therefore, the legislation violated Article 8 of the European Convention on Human Rights.[16][17]
Yarovaya law[edit]
Main article: Yarovaya law
In July 2016, President Vladimir Putin signed into law two sets of legislative amendments commonly referred to as the Yarovaya law, after their key author, Irina Yarovaya, a leading member of the ruling party United Russia. The new regulations will take effect on July 1, 2018.
According to the amendments, Internet and telecom companies are required to disclose communications and metadata, as well as "all other information necessary," to authorities, on request and without a court order.[18]

